A new phishing-as-a-service (PhaaS) kit known as Sneaky 2FA has been observed deploying an advanced “Browser-in-the-Browser” (BitB) attack technique. The Hacker News+2Push Security+2 This evolution in phishing attacks presents heightened risks for organizations relying on standard two-factor authentication (2FA) and demonstrates how accessible sophisticated tools have become for low-skill threat actors.
What is the Browser-in-the-Browser attack?
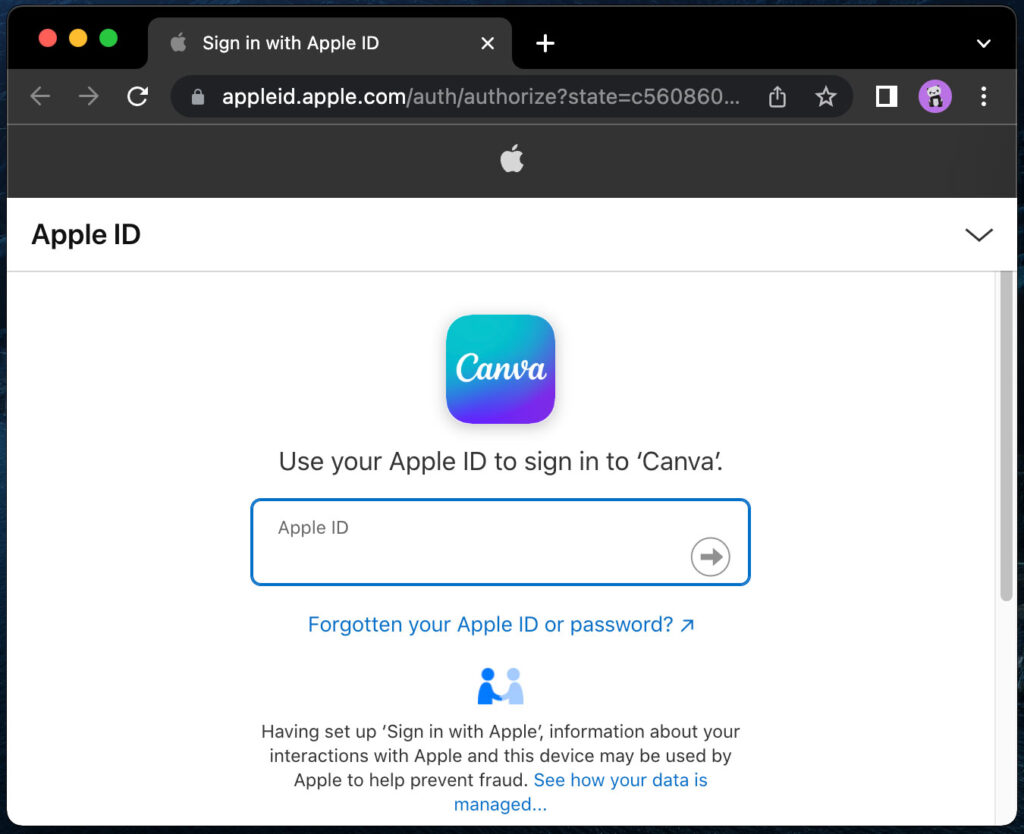
In a BitB attack, a phishing page presents a fake browser window within a web page that mimics the real browser interface, complete with an address bar showing a legitimate URL. Users believe they are interacting with a genuine login prompt when in fact the interface is crafted entirely in HTML and CSS and controlled by an attacker-hosted server. The Hacker News+1
In the case of Sneaky 2FA the exploit flow looks like this:
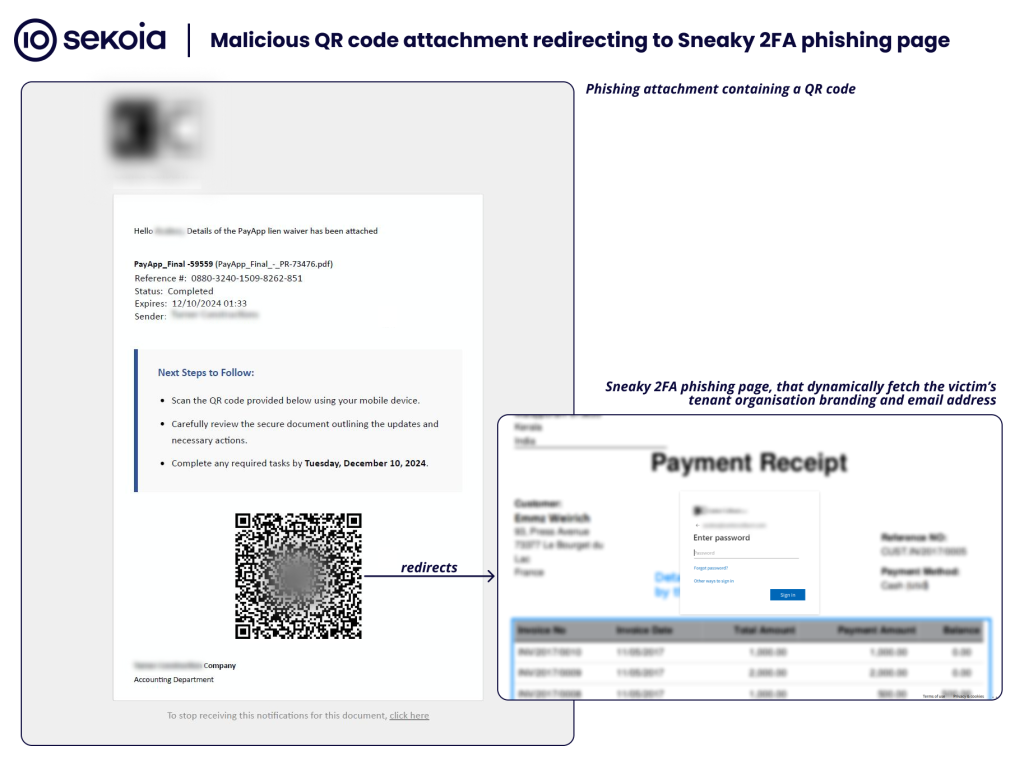
- The victim visits a phishing domain (for example disguised as a document viewer). Push Security+1
- The site uses bot-protection (such as a CAPTCHA or Turnstile) to filter out automated or security-tool access. The Hacker News+1
- The victim is presented with a “Sign in with Microsoft” type button. Once clicked, a fake login window appears inside the page, styled to look like a native pop-up, and the user enters credentials. The Hacker News+1
- The attacker immediately captures username, password, session tokens or MFA codes and uses them for account takeover. Push Security+1
Why this is particularly dangerous
- Because it mimics the browser UI so convincingly, many users won’t realise they are entering credentials into a controlled form rather than a secure browser interface.
- Password managers may refuse to autofill in these embedded fake windows, which can itself become a red flag for vigilant users. Malwarebytes
- The kit uses domain rotation, short-lived infrastructure and contextual checks (user agent, geolocation, referral) to remain undetected longer. Push Security+1
- Many organizations assume that enabling standard 2FA is sufficient to prevent account takeover, but exploitation of session cookies, tokens or phishing of credentials during or after MFA renders this assumption unsafe.
- The availability of this kit as a service lowers the barrier to entry for attackers, allowing even low-skill actors to deploy highly convincing phishing campaigns. The Hacker News+1
Indicators of compromise and workflows to monitor
- Unusual login prompts appearing to come from trusted services but triggered unexpectedly when users click links.
- Browser sessions where expected URL autofill or password-manager autofill fails (especially for known services).
- Phishing domains which require CAPTCHA or bot-challenge before showing login interface (may indicate malicious filtering). Push Security
- Session cookie theft or MFA bypass events—monitor for anomalous device access, impossible travel, same-session reuse from different IPs/devices.
- Rapid domain creation or short-lived domains used in credential captures then dropped.
- Browser pop-ups requesting credential entry when users believe they are interacting within an embedded content viewer or other non-authentication flow.
Defensive actions to strengthen protection
- Encourage or enforce use of phishing-resistant MFA (FIDO2 keys, hardware tokens) rather than only SMS or push notifications.
- Deploy password managers and educate users that absence of autofill on known login forms may signal a fake prompt.
- Monitor and block access to credential capture domains and apply filtering on newly registered or recently active domains with low history.
- Use conditional access policies restricting logins to known devices, geolocations, and visible session attributes.
- Train users to recognise browser-in-the-browser styled attacks: e.g., pop-ups with address bars inside a page rather than the native browser UI.
- Ensure incident response teams include phishing kit-related flows (e.g., credential harvesting, token misuse) rather than purely malware-download detection.
Final thoughts
The evolution of Sneaky 2FA to include Browser-in-the-Browser functionality illustrates how phishing campaigns remain a leading vector for account takeover despite widespread availability of multi-factor authentication. Organizations must assume attackers are capable of replicating trusted interfaces and stealing credentials, session cookies, or MFA tokens. A layered defense combining phishing-resistant MFA, password managers, behavioral monitoring and user training is required to stay ahead.
Sign up For Newsletter!!









Leave a Reply