Salesforce has launched an investigation into customer data exposure that appears to be linked to a third party integration involving Gainsight applications. The incident did not originate from a flaw in the Salesforce core platform. Instead it appears attackers abused trusted application connections that were already authorized to access Salesforce environments.
This type of incident highlights a growing risk in modern cloud ecosystems where trusted integrations can become weak entry points for attackers. Even when a primary platform remains secure the connected applications and their access permissions can expose sensitive information.
What Happened
The activity was detected when unusual access patterns were observed tied to applications published by a third party vendor. These applications were previously authorized by Salesforce customers to connect to their environments. Once suspicious behavior was confirmed Salesforce immediately revoked active access tokens associated with those integrations to prevent further data exposure.
Attackers likely leveraged previously established permissions that allowed the connected application to read or extract customer data without needing to breach the main Salesforce infrastructure.
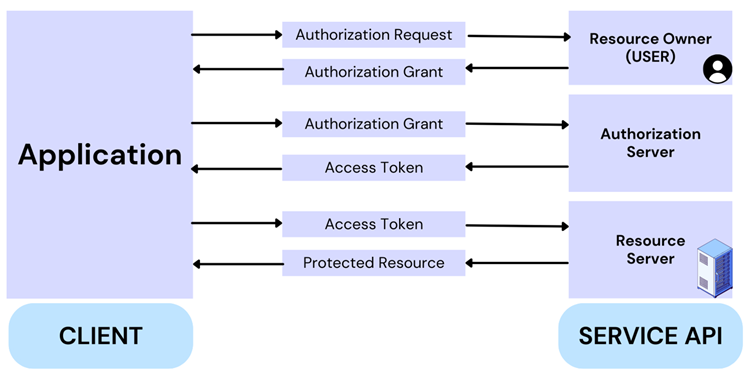
How the Attack Likely Worked
The integration relied on permission tokens that allowed the third party application to communicate directly with Salesforce environments. Once attackers gained access to these tokens they could access permitted data without raising immediate alarms.
Because these integrations are commonly used for business analytics customer success operations and automation they often have broad access permissions. This increases risk exposure when they are compromised.
Why This Matters
This incident demonstrates the growing danger of supply chain and integration based attacks. Many organizations assume their cloud providers are secure but fail to fully monitor or restrict the access granted to connected third party tools.
A breach through a trusted application can be just as damaging as a direct breach of the primary platform. Customer records internal communications and sensitive business data can all be exposed through these indirect access paths.
What Organizations Should Do
Organizations using Salesforce or any large cloud platform should immediately review all connected third party applications.
Access permissions should be reviewed and reduced using least privilege principles.
Unused or unnecessary integrations should be removed.
All access tokens should be rotated and logs reviewed for unusual access behavior.
Security teams should treat third party integrations as high risk assets and include them in monitoring and incident response workflows.
Lessons for the Future
Incidents like this show that cloud security is no longer only about protecting the primary platform. Every integration and connection expands the attack surface. Organizations must treat integrations as privileged access pathways and secure them accordingly.
Trust should never be assumed purely because an application is widely used or officially published. Continuous monitoring periodic access reviews and strong token management are now essential to protecting customer data.
Final Thoughts
This investigation serves as a strong reminder that modern cyber threats often exploit trust relationships rather than technical vulnerabilities. By tightening controls over third-party integrations and improving visibility into connected applications organizations can significantly reduce their risk of data theft and unauthorized access.
Sign up For Newsletter!!










Leave a Reply