

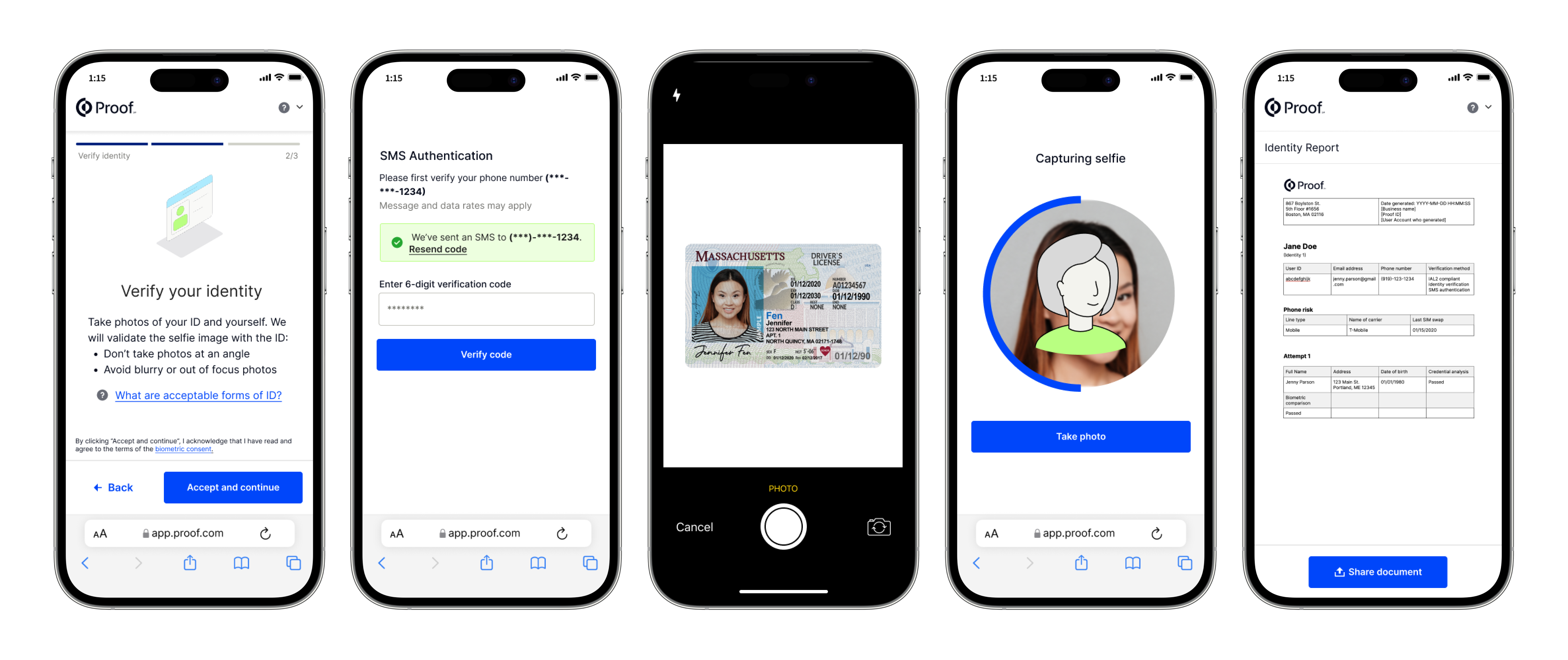
Security researchers have uncovered a large scale operation in which North Korean threat actors are targeting engineers and technology professionals worldwide with an unusual and deceptive proposal. Instead of asking victims to perform technical work the attackers attempt to rent their identities. These identities are then used to pose as legitimate IT workers inside global companies enabling the regime to infiltrate corporate networks generate revenue and bypass international sanctions imposed on North Korea.
This activity represents a sophisticated evolution of North Korea’s long standing strategy of weaponizing the global gig economy. By using real engineers as unwitting fronts the attackers create a credible digital footprint that blends into the workforce of multinational organizations. This allows them to obtain employment contracts, handle sensitive systems and gain access to company environments they would never be able to reach directly.
How the Identity Rental Scheme Works
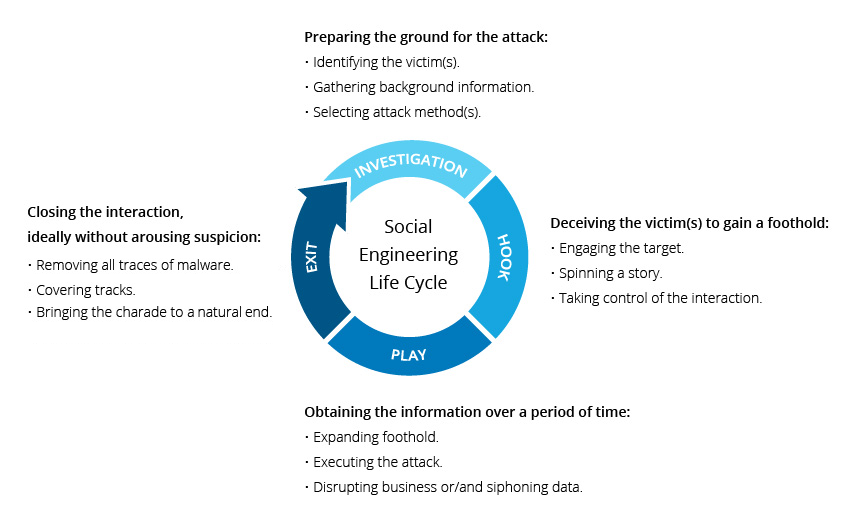


The operation typically begins with unsolicited messages delivered through email professional networks or freelance job platforms. Victims are offered unusually high compensation simply for allowing someone else to use their name and account credentials on job applications. The attackers claim they need help overcoming geographical restrictions or account verification challenges.
Once an engineer agrees to participate the threat actors use the victim’s identity to register on employment portals conduct interviews and secure remote technical work contracts. The real engineer never performs any of the job responsibilities. Instead North Korean operatives take over the role, impersonating the victim and performing sensitive technical tasks under the stolen identity.
The attackers also request additional personal data including identification documents facial verification images two factor authentication codes and device fingerprints. This information allows them to build a full employment profile that appears legitimate to companies hiring remote engineers.
Why This Scheme Is So Dangerous
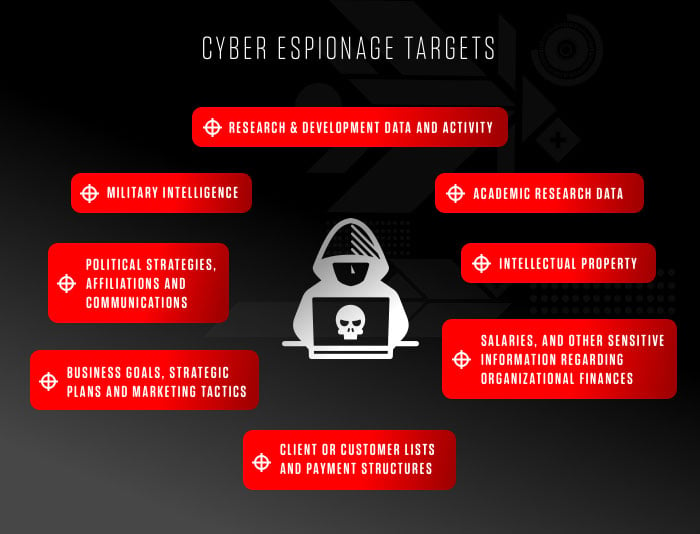

Allowing a hostile state actor to work inside a company under a stolen identity creates one of the most serious security exposures a business can face. These operatives receive direct access to code repositories cloud services administrative tools and sensitive infrastructure depending on the job role they obtain.
The risks include:
• Unauthorized access to proprietary systems
• Theft of intellectual property
• Manipulation of production environments or source code
• Insertion of backdoors or malware into software supply chains
• Data exfiltration through legitimate employee channels
• Long term persistence inside corporate networks
Because the attackers appear as real employees the usual security alerts associated with unknown accounts or suspicious geolocations may not trigger. This makes detection extremely difficult and allows the operation to continue for months or even years.
This scheme also gives North Korea access to foreign currency at scale. By infiltrating legitimate companies and collecting engineer salaries the regime can funnel money back into its cyber programs and weapons development.
Tactics Used to Maintain Disguise and Persistence



North Korean operatives are known for their disciplined social engineering capabilities and operational patience. After securing a job under a stolen identity they use multiple layers of technical and behavioral deception to maintain their cover.
These tactics include:
Imitating the communication style of the person whose identity they stole
Using residential proxy networks to mimic the victim’s regional internet traffic
Logging in during the victim’s normal business hours
Avoiding video calls and requesting audio only meetings
Using remote desktop tools hosted on virtual machines that replicate the victim’s system settings
Providing excuses such as camera failures or travel to avoid visual verification
This level of operational mimicry allows them to remain undetected even in companies with strong hiring and monitoring procedures.
Global Scale and Impact on the Technology Sector

This identity rental campaign is not isolated. Security teams across multiple continents have reported patterns of suspicious activity involving remote IT worker impersonation linked to North Korean groups. These incidents affect software development, QA engineering, DevOps, cloud management and technical support roles.
The broader impact on the technology sector is substantial:
Companies unknowingly onboard hostile nation state actors
Contractors are exposed to legal and financial consequences for identity misuse
Supply chain dependencies become compromised
Regulated industries face compliance violations
Critical infrastructure operators suffer increased espionage risk
Because remote work has become normalized globally this attack model fits perfectly into the modern workforce landscape.
How Organizations Can Defend Against Identity Rental Schemes


Organizations must treat remote hiring with the same seriousness as granting administrative access to internal systems. Several controls can dramatically reduce exposure to identity rental schemes.
Conduct strict identity verification during onboarding
Require real time live video verification when hiring remote workers
Use continuous identity assurance tools that detect unusual access behavior
Monitor impossible travel patterns and session anomalies
Restrict access based on least privilege
Audit contractor accounts frequently
Prohibit the outsourcing of credentials or job responsibilities
Educate HR and recruiting teams about this specific threat
Companies should also deploy zero trust principles that authenticate not only the user but also the device network and context of every login.
Final Analysis
North Korea’s identity rental scheme is a significant escalation in global cyber operations. By recruiting real engineers and using their identities as camouflage threat actors can move through legitimate hiring channels and operate from inside trusted environments. This gives them unprecedented access to technical infrastructure intellectual property and financial resources.
The combination of remote work trends and the global talent shortage makes this threat particularly effective. Organizations must adopt stronger verification controls and continuous monitoring to ensure that the people working inside their systems are who they claim to be.
Sign up For Newsletter!!










Leave a Reply