A newly emerging ransomware-as-a-service (RaaS) platform named ShinySp1d3r has been uncovered. It is being developed by threat actors associated with the groups known as ShinyHunters and Scattered Spider.
Who is behind it
The development of ShinySp1d3r is being led by the extortion group ShinyHunters, in collaboration with affiliates of Scattered Spider and LAPSUS$ under a collective identity. The RaaS will be operated by the known actors while providing affiliates access to the encryptor and infrastructure.
Key features of the encryptor
The sample of the encryptor shows several advanced features including:
- Hooking of the Windows Event Tracing function to prevent event logs from capturing its actions.
- Termination of processes that hold handles to files the ransomware wants to encrypt. This includes using mechanisms to kill those processes and optionally using a restart-manager API (though not fully implemented yet).
- Filling free disk space by creating random temporary files to overwrite deleted data, thereby making recovery more difficult.
- Deleting shadow volume copies so that Windows system restore mechanisms are disabled.
- Searching for network shared hosts and attempting to encrypt files across the network.
- Using encryption algorithms: the ransomware uses ChaCha20 to encrypt file content and protects the private key using RSA-2048 for each file.
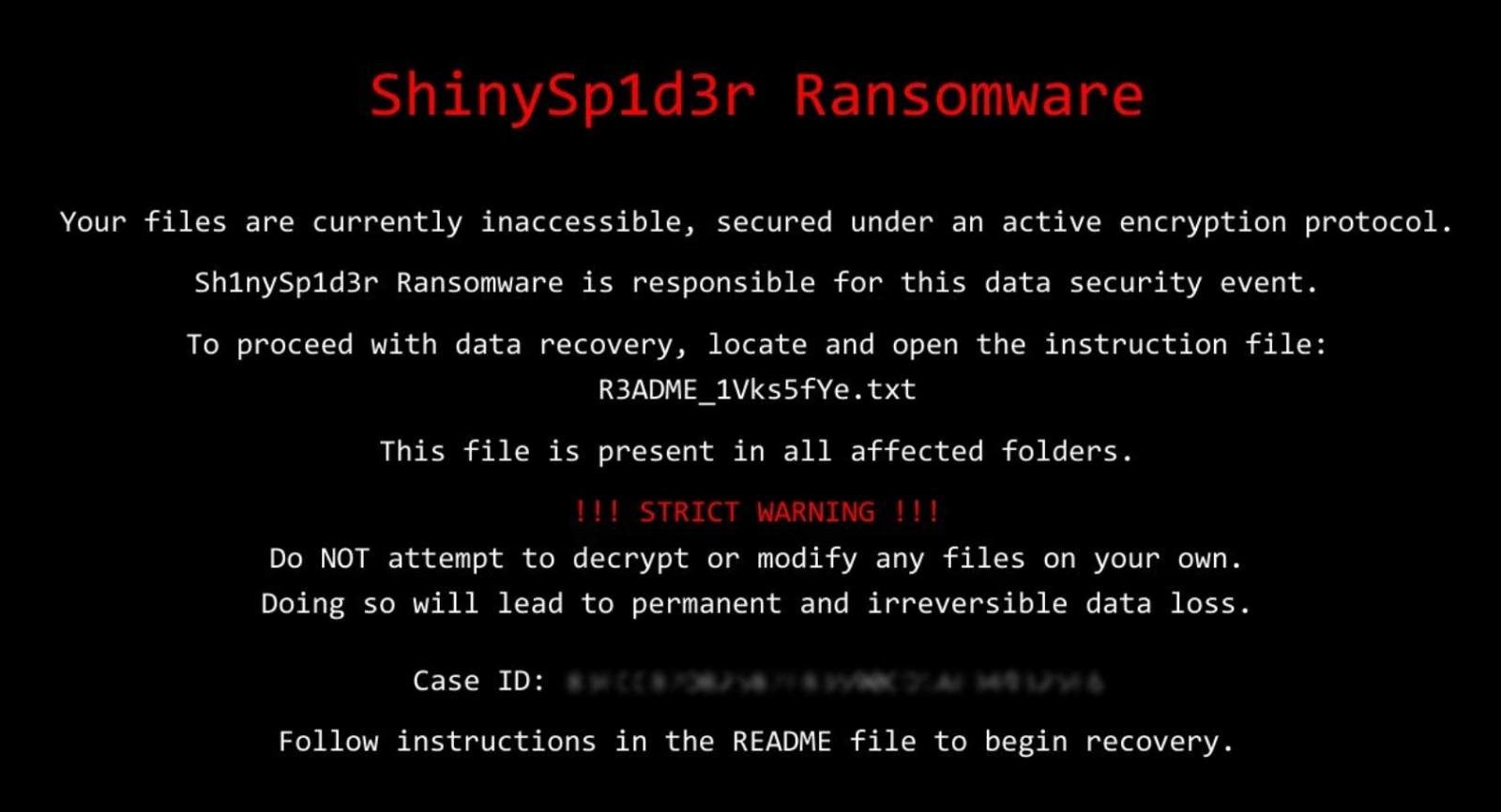
- Each encrypted file is marked with a custom extension derived via a mathematical formula and includes a file header beginning with “SPDR” and ending with “ENDS”, containing metadata, the encrypted key and file details.
- Propagation methods that include service creation, WMI execution, and GPO startup script deployment.
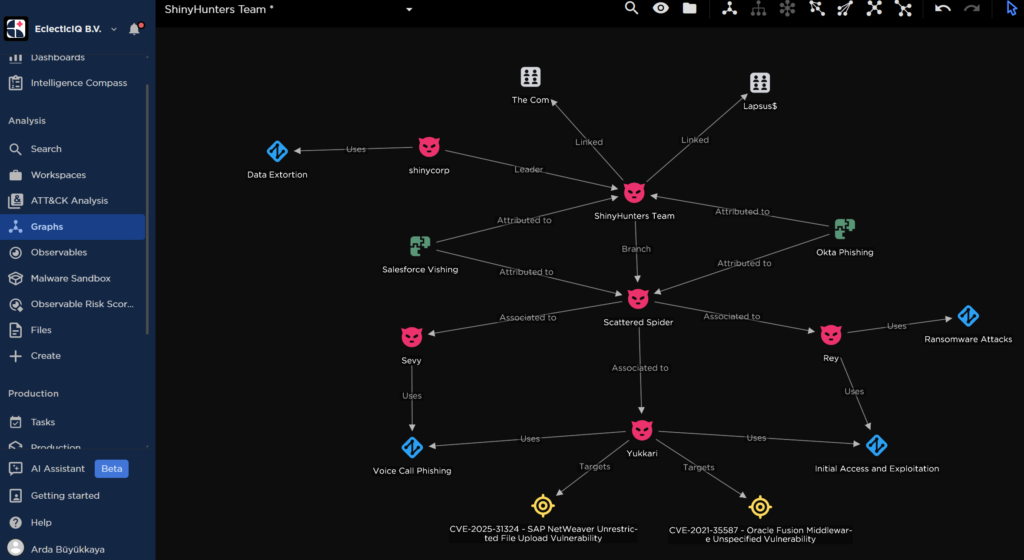
Operational aspects and targeting
The ransomware RaaS is still in development but already functional in preview build form. It is designed to be offered to affiliates. The threat actors claim they will avoid targeting certain sectors — for example they say healthcare providers and Russian/CIS region companies will not be targeted. However, such claims historically are not always honored.
Why this matters to organizations
This new platform brings several risks:
- Because it is built from scratch and not merely a rebranded older encryptor the threat may evolve rapidly.
- The advanced feature set means that detection and remediation may become more complex.
- Organizations may become victims via indirect affiliation of the RaaS rather than direct targeted attacks.
- If multiple affiliates launch attacks simultaneously this could lead to large scale incidents across sectors.
- The claimed “exclusion list” of sectors or regions may lull some organizations into lower preparedness even though they may still be at risk.
What you should do
- Conduct a comprehensive inventory of your endpoint and server estate and check for ransomware-prevention controls.
- Ensure backups are complete, tested and offline / immutable if possible so that encryption does not become catastrophic.
- Monitor for abnormal file access patterns, new service or WMI deployments, unusual process creation, and modifications of shadow volume stores or backup file sets.
- Review network share access and segmentation to reduce the impact of ransomware spreading laterally.
- Train incident response teams in ransomware outbreak scenario including containment, communication, negotiation (if allowed) and forensic readiness.
- Stay updated on threat intelligence for further indicators of compromise linked to ShinySp1d3r so you can adapt detection and response strategies.
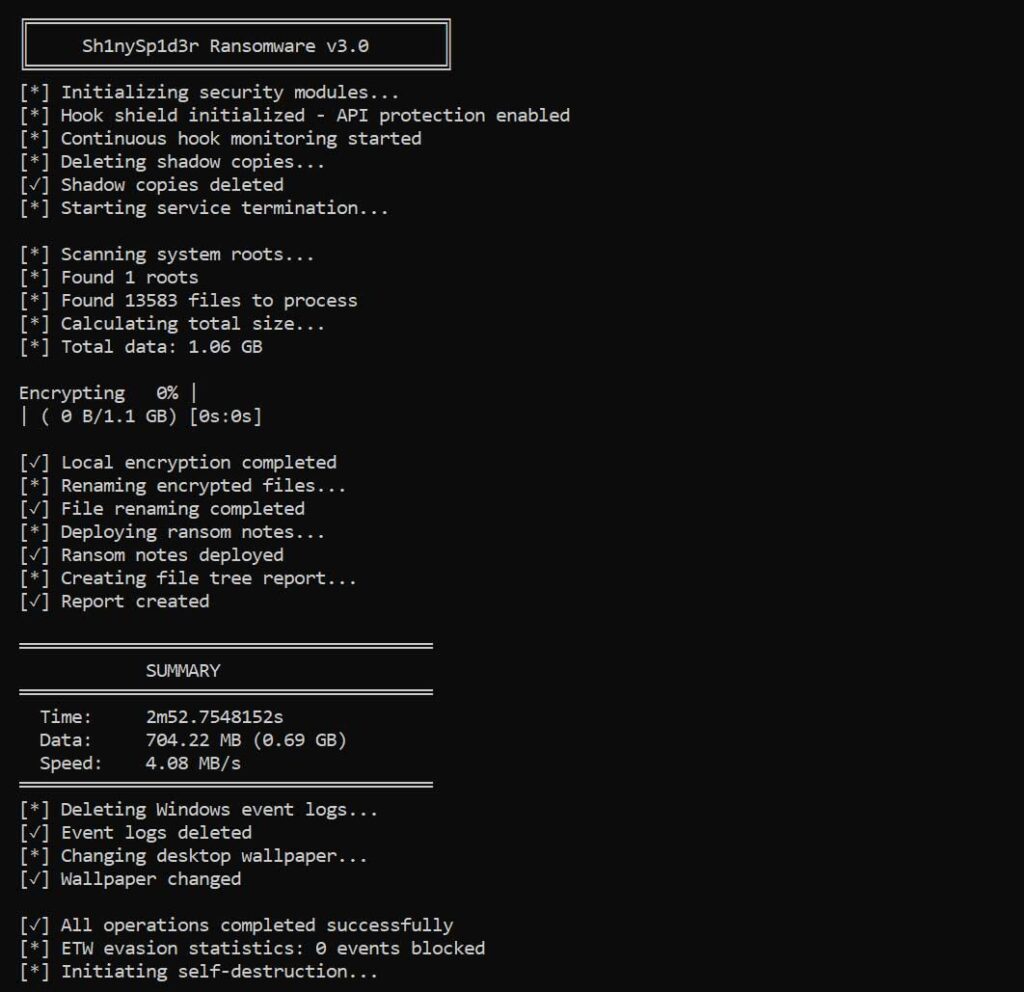
Final thoughts
ShinySp1d3r signals the continued evolution of ransomware as a service from the ground up rather than simply leveraging existing encryptors. For enterprises and cybersecurity teams this means the threat surface is expanding and becoming more modular. Taking proactive steps now will strengthen resilience and reduce risk of major disruption.
Sign up For Newsletter!!









Leave a Reply