

Cybercriminals have launched a new phishing campaign that uses fake Calendly style meeting invitations to impersonate major global brands. The objective is simple but dangerous. Attackers aim to trick victims into granting access to their advertising management accounts which include Meta Ads Google Ads and other marketing platforms. Once the attackers gain control of these accounts they immediately begin running unauthorized ads costing organizations significant financial losses while enabling the distribution of harmful or fraudulent content.
This campaign demonstrates how threat actors are refining social engineering tactics by blending trusted business tools with corporate brand impersonation. Calendly is widely used for scheduling meetings which gives these malicious invitations a natural sense of legitimacy. When paired with logos of top brands the phishing lures appear highly convincing even to experienced users.
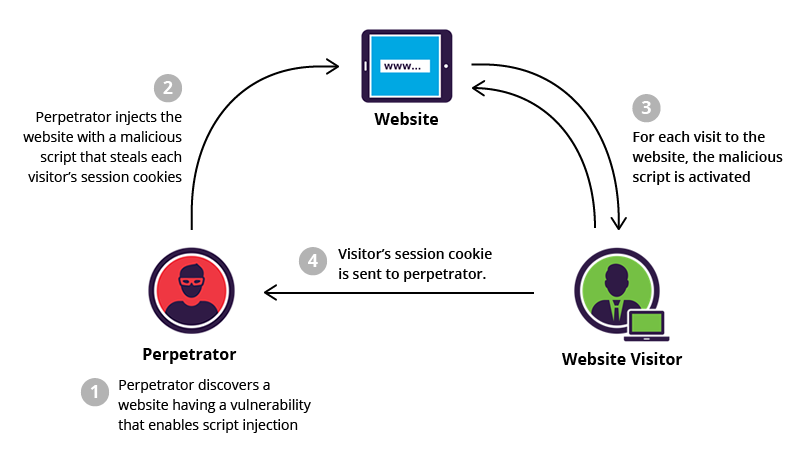
How the Attack Works


The attack begins when potential victims receive a meeting invitation that appears to come from a well known organization. The message looks identical to a real scheduling request. It includes a meeting title a proposed time and a call to action prompting the user to confirm or review the details of the meeting.
Clicking the link does not take the user to a real Calendly page. Instead the victim is redirected through a series of attacker controlled websites designed to harvest credentials or trick users into approving third party app permissions. These permission prompts often request access to advertising accounts or business management platforms.
Once the victim unknowingly grants access the attacker immediately gains administrative control over the ad manager account. From there they begin launching unauthorized ad campaigns promoting scams malware distribution sites or fraudulent investment offers.
What makes this attack particularly effective is the use of major corporate brands in the email headers. Victims are more inclined to trust the request when the sender appears to be a large recognizable company. The professionalism of the fake Calendly invitation further reduces suspicion.
Why Ad Manager Accounts Are a High Value Target



Ad manager accounts are extremely valuable to cybercriminals because they allow attackers to spend real money through someone else’s business infrastructure. These platforms can deploy large advertising budgets quickly and at scale which makes them an attractive tool for fraud operations.
Once attackers take control of an organization’s advertising account they can:
• Run malicious ad campaigns promoting scams
• Spread malware through deceptive advertisements
• Redirect traffic to phishing pages
• Promote fraudulent investment schemes
• Damage the organization’s reputation and brand integrity
Attackers also commonly adjust account notification settings to hide their activity for as long as possible. By the time the victim notices unusual charges substantial financial damage may already have occurred.
Growing Trend of Phishing Through Productivity Tools


The use of productivity tools such as scheduling apps online document platforms and collaboration systems has become a preferred attack method for cybercriminals. These services are visually familiar and trusted by business users making them fertile ground for social engineering.
By mimicking legitimate Calendly invitations attackers bypass traditional email security filters which tend to focus on suspicious attachments or uncommon sender behavior. Since the emails look identical to typical business communication fewer security warnings are triggered.
This campaign is also part of a broader surge in brand spoofing where attackers copy the identity of major companies to create believable phishing lures. Victims mistakenly assume that the communication has undergone corporate level security controls and therefore trust the request without further verification.
How Organizations Can Protect Their Advertising and Business Accounts

Defending against this attack requires a mix of technical controls and user awareness. Organizations should:
Enable strict multi factor authentication on all business and advertising accounts
Monitor ad account activity for sudden changes in spending behavior
Restrict administrative permissions and use role based access controls
Educate employees about phishing campaigns that mimic scheduling tools
Encourage verification of unsolicited meeting invitations before clicking
Use email security tools capable of detecting brand impersonation patterns
Businesses should also conduct periodic audits of advertising accounts to ensure no unknown apps or third party integrations have been granted access.
Final Analysis
This phishing campaign reinforces a critical truth in cybersecurity. Attackers no longer rely on outdated email lures or crude deception. Instead they exploit trusted business workflows and professional grade branding to create highly convincing attacks. Fake Calendly invitations paired with corporate logo impersonation are effective because they blend seamlessly into daily business operations.
Organizations must train teams to approach every unexpected meeting invitation with caution especially when the link prompts permission approvals or redirects to unfamiliar pages. The theft of advertising accounts is financially damaging and can be exploited to distribute large scale fraud or harmful content. Strong identity protection user training and continuous monitoring are essential to preventing account compromise.
Sign up For Newsletter!!










Leave a Reply