


The Cybersecurity and Infrastructure Security Agency is warning organizations across the United States about an advanced cyber campaign linked to Chinese state sponsored threat actors. The operation uses a new strain of malware known as BrickStorm to compromise VMware servers and maintain long term access inside targeted networks.
This attack represents a significant escalation because it exploits virtualization infrastructure which is often considered a secure backbone for enterprise workloads. Once inside a VMware environment, attackers can move laterally with minimal detection gain high privilege access and conduct wide ranging espionage activities.
How BrickStorm Infects VMware Systems


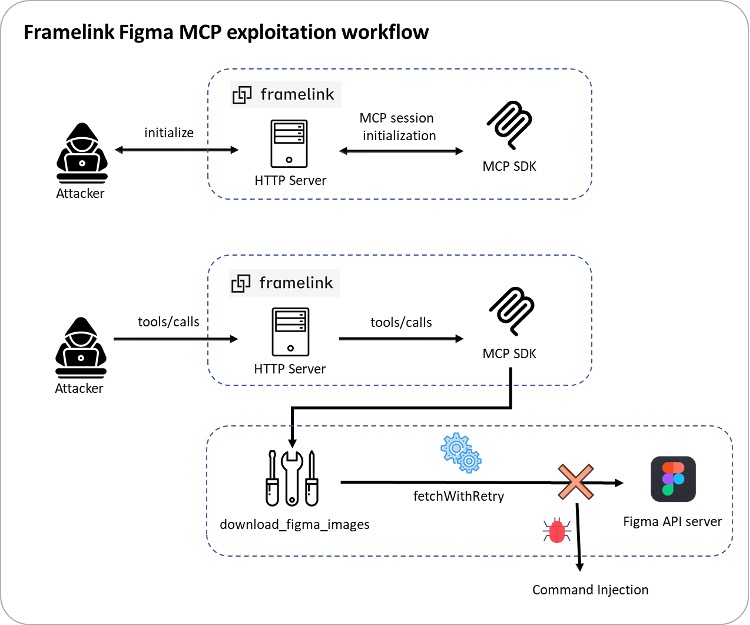
BrickStorm is engineered specifically to target VMware systems including servers that host virtual machines for entire corporate environments. The malware is deployed by exploiting server vulnerabilities or stolen administrative credentials. Once executed BrickStorm installs a hidden backdoor allowing attackers to issue commands retrieve data and deploy additional payloads.
The malware focuses on stealth. It disguises its activity using native VMware service patterns avoids generating high volume network traffic and modifies logs to prevent administrators from discovering the compromise. Because virtualized environments often host critical workloads any compromise at this layer has far reaching consequences.
The sophistication of BrickStorm indicates that the operators behind it have strong knowledge of enterprise virtualization. They understand how VMware environments are structured and how defenders monitor them. This intelligence allows the threat actors to bypass traditional detection strategies.
Capabilities and Objectives of BrickStorm Operators


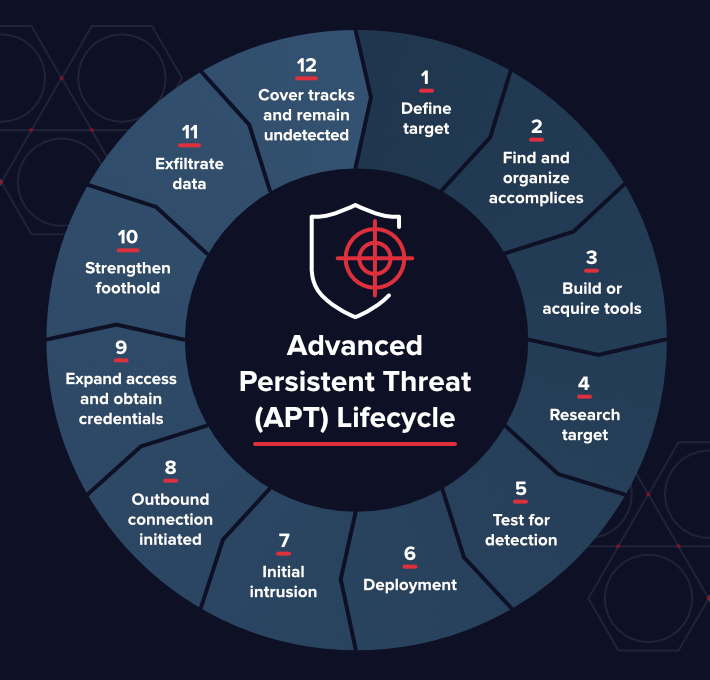
The actors using BrickStorm pursue long term espionage rather than immediate financial gain. Their tactics tools and infrastructure match Chinese state sponsored advanced persistent threat groups known for highly targeted campaigns.
Once established on a VMware server BrickStorm enables:
Collection of sensitive files stored within virtualized environments
Access to multiple virtual machines from a single compromised host
Lateral movement into internal applications and databases
Credential harvesting to expand access
Deployment of secondary implants for specialized tasks
Quiet exfiltration of data through encrypted communication channels
Because VMware hosts often sit at the core of corporate networks the malware provides attackers with a strategic vantage point. This allows them to observe internal operations capture sensitive information and maintain persistence even if individual systems are remediated.
Why VMware Infrastructure Is a High Value Target



Virtualized environments are attractive to nation state operators because they function as centralized gateways for corporate operations. Attacking the virtualization layer grants access to dozens or hundreds of machines without needing to compromise them individually.
VMware servers typically support:
Email and messaging systems
Databases and file servers
Application hosting environments
Security tooling
Authentication services
Domain controllers
Gaining access to this layer effectively allows complete visibility into enterprise activity. It also enables attackers to hide themselves inside legitimate operational traffic which makes detection extremely challenging. Because VMware hosts rely heavily on trust relationships BrickStorm is able to spread or maintain persistence even when defenders enforce strong endpoint security on individual machines.
What Makes BrickStorm a Significant National Security Concern


CISA issued its warning because the campaign specifically targets critical infrastructure sectors financial services telecommunications health care and government affiliated networks. These environments hold sensitive data and support essential operations.
BrickStorm’s design suggests it was built for strategic intelligence collection. Nation state groups often use malware like this to map network structures identify high value targets and quietly exfiltrate sensitive information.
Because the compromise occurs at the virtualization layer the malware may survive system reboots host reconfiguration and even some remediation attempts. This persistence makes it an ideal espionage tool capable of operating undetected for extended periods.
How Organizations Should Respond to the BrickStorm Threat

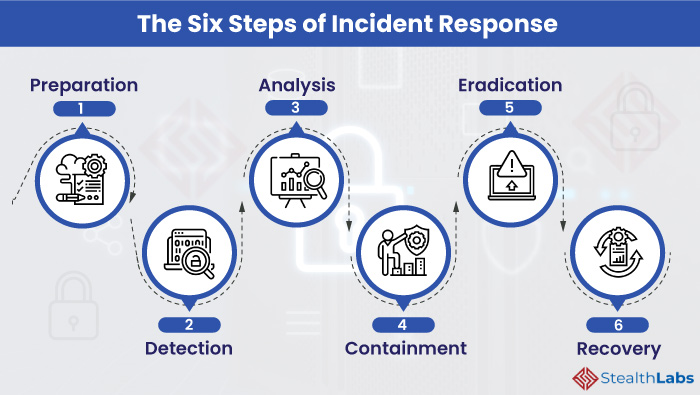

Organizations using VMware should immediately implement enhanced monitoring integrity controls and patch management. Recommended actions include:
Conduct full audits of VMware hosts for unusual files processes or network connections
Apply the latest VMware security patches across ESXi vCenter and related services
Review authentication logs for unexpected administrator activity
Isolate systems exhibiting suspicious behavior
Deploy endpoint detection tools capable of inspecting virtualization level activity
Rotate privileged credentials and remove unused administrative accounts
Enable strict access controls to limit lateral movement
Because BrickStorm focuses on stealth organizations must go beyond routine perimeter monitoring. Specialized visibility into virtual machine management APIs and hypervisor interactions is essential.
Final Analysis
BrickStorm represents a serious evolution in nation state cyber capabilities. By targeting VMware servers Chinese threat actors are aiming directly at the operational core of enterprise networks. This gives them unparalleled access to sensitive systems while allowing attacks to remain covert.
CISA’s warning underscores the urgency for organizations to strengthen defenses around virtualization infrastructure. Traditional endpoint security alone is insufficient when the attack originates from the hypervisor layer. Enterprises must adopt deeper monitoring strategies apply patches rapidly and harden access to their virtualization platforms.
Sign up For Newsletter!!










Leave a Reply