The developers behind Notepad Plus Plus have released a security update addressing a critical flaw in the application’s update mechanism…
Read More

The developers behind Notepad Plus Plus have released a security update addressing a critical flaw in the application’s update mechanism…
Read More
Google has released an emergency security update for its Chrome browser after confirming the existence of a previously unknown zero…
Read More
A new wave of cyberattacks linked to the threat group known as Silver Fox is targeting global organizations through deceptive…
Read More
The Cybersecurity and Infrastructure Security Agency is warning organizations across the United States about an advanced cyber campaign linked to…
Read More
A major data breach involving the third party analytics provider Marquis has exposed sensitive customer information belonging to more than…
Read More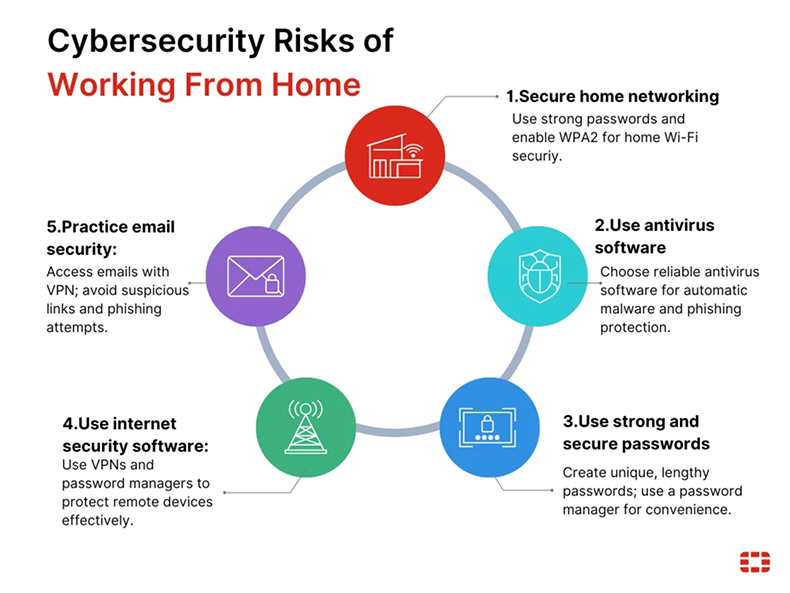
Security researchers have uncovered a large scale operation in which North Korean threat actors are targeting engineers and technology professionals…
Read More
Cybercriminals have launched a new phishing campaign that uses fake Calendly style meeting invitations to impersonate major global brands. The…
Read More
A large scale investigation into public GitLab Cloud repositories has uncovered a significant and alarming security problem. A security researcher…
Read More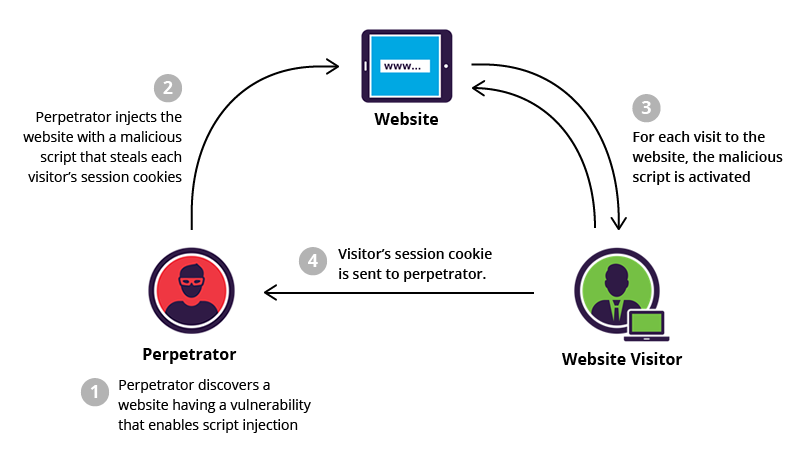
Microsoft has announced a significant enhancement to its Entra ID authentication pipeline designed to protect users from a growing class…
Read More
A serious insider threat incident has placed the cybersecurity industry on high alert after an employee at CrowdStrike was caught…
Read More