How to Review and Patch High Severity CVEs 53
This is a long cybersecurity demo article for BreachWave. It is written so that blog, magazine and security theme layouts in WordPress can show headings, lists and images.
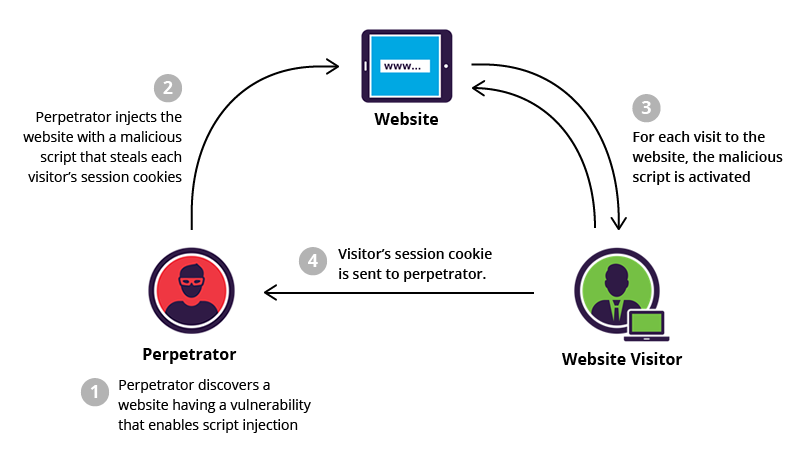
What happened A security team noticed activity related to cloud security in production. The alerts came from SIEM correlation rules and from an EDR agent. The purpose of this post is to document the indicators and the response so other analysts can repeat it.
Detection ideas
- Look for rare outbound connections to IP addresses that are not in your allow list.
- Alert on sign ins from countries that your business does not operate in.
- Inspect mail gateway logs for phishing attempts using the same subject.
- Send the indicators to EDR, firewall and mail security tools.
Response steps
- Isolate the affected device.
- Reset any exposed accounts and enable MFA.
- Collect evidence and keep timeline notes.
- Notify the owner of the affected system.
- Update the incident runbook with what worked.
This text is just a starter. Replace IPs, hashes and internal names with your own real values after import.
Sign up For Newsletter!!