

The developers behind Notepad Plus Plus have released a security update addressing a critical flaw in the application’s update mechanism after reports surfaced of traffic hijacking during update checks. The vulnerability exposed users to the risk of receiving manipulated update information which could potentially redirect them to malicious infrastructure.
Updater mechanisms are a high value target for attackers because they operate with user trust and often elevated permissions. Any weakness in how updates are delivered or verified can be abused to distribute malicious payloads at scale. In this case the flaw enabled adversaries positioned on the network path to interfere with update traffic and inject unauthorized responses.
How the Update Traffic Was Hijacked
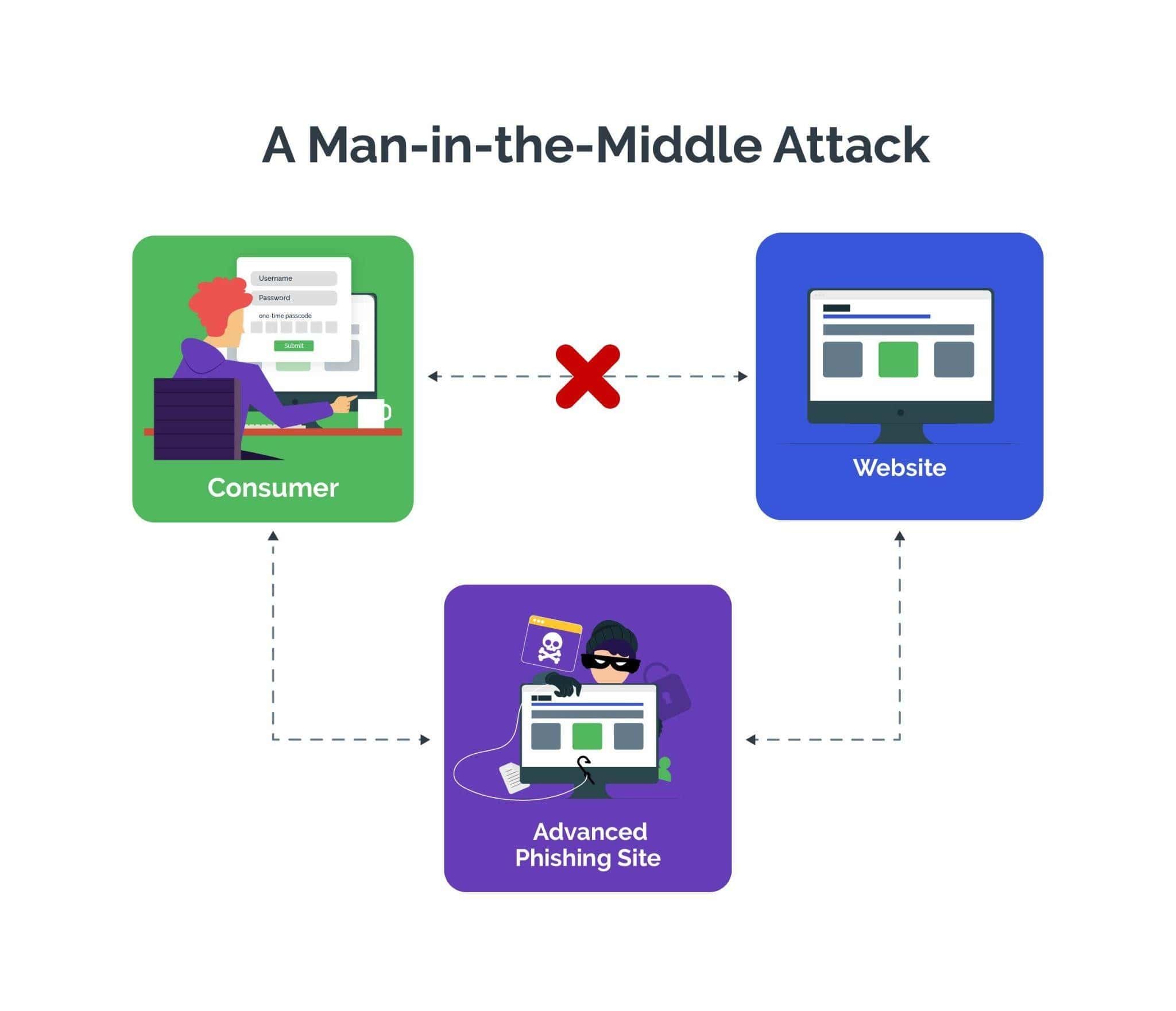

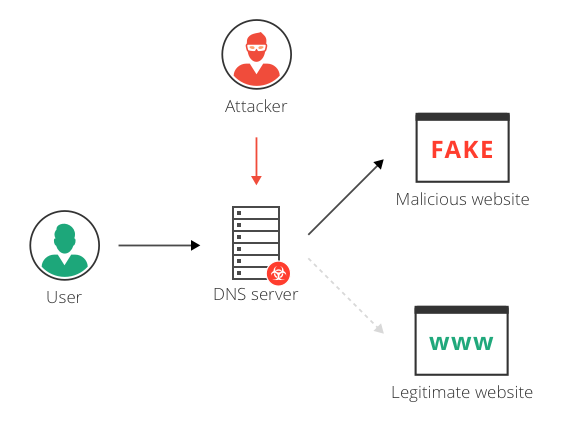
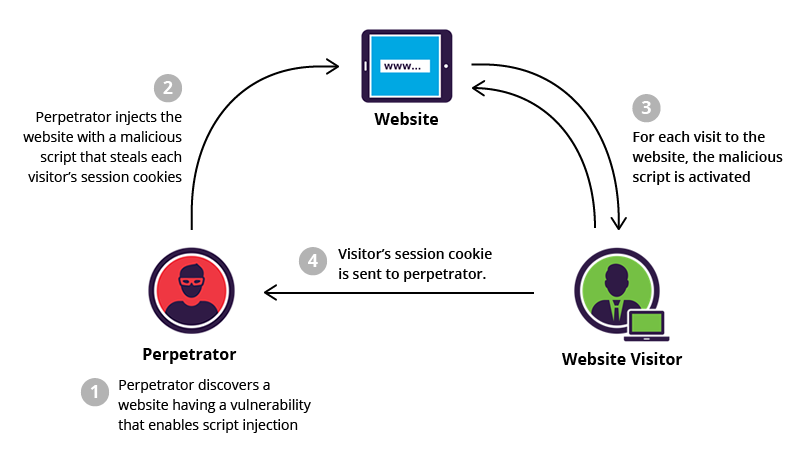
The issue stemmed from how the updater retrieved version and download information from remote servers. Under certain conditions update requests could be intercepted and altered by a malicious actor capable of performing a man in the middle attack. This typically occurs on compromised networks insecure wireless connections or environments where traffic inspection is abused.
By manipulating the update response an attacker could redirect the application to a rogue server or provide falsified metadata. While no confirmed large scale malware distribution was publicly disclosed the exposure created a dangerous opportunity. Attackers could leverage this position to deliver trojanized binaries or trick users into installing malicious components under the guise of a legitimate update.
Why Updater Flaws Are Especially Dangerous

Update mechanisms sit at the heart of software trust. Users expect updates to be safe authentic and integrity protected. When an updater is compromised attackers bypass traditional security controls because the malicious content is delivered through a trusted channel.
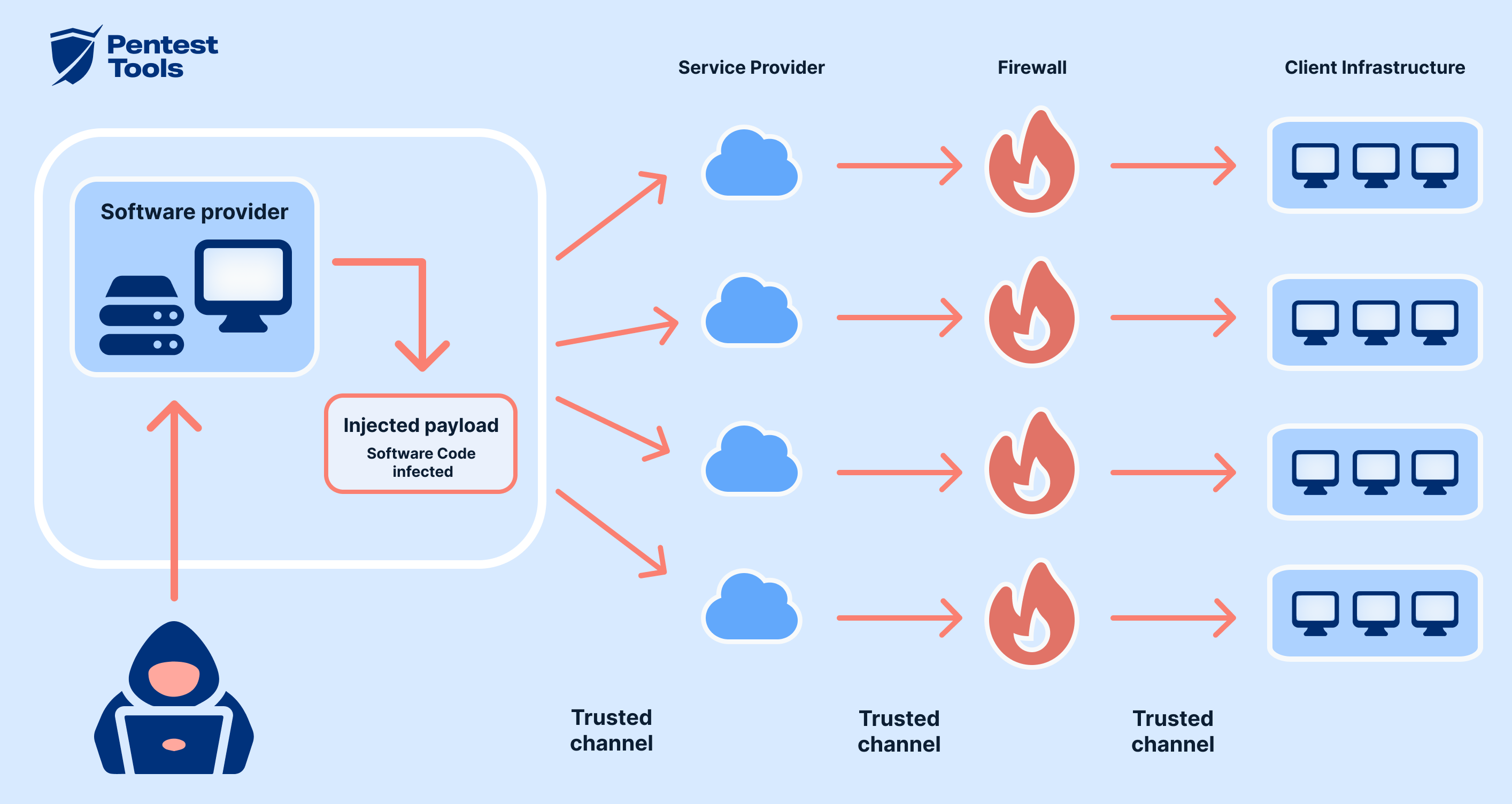
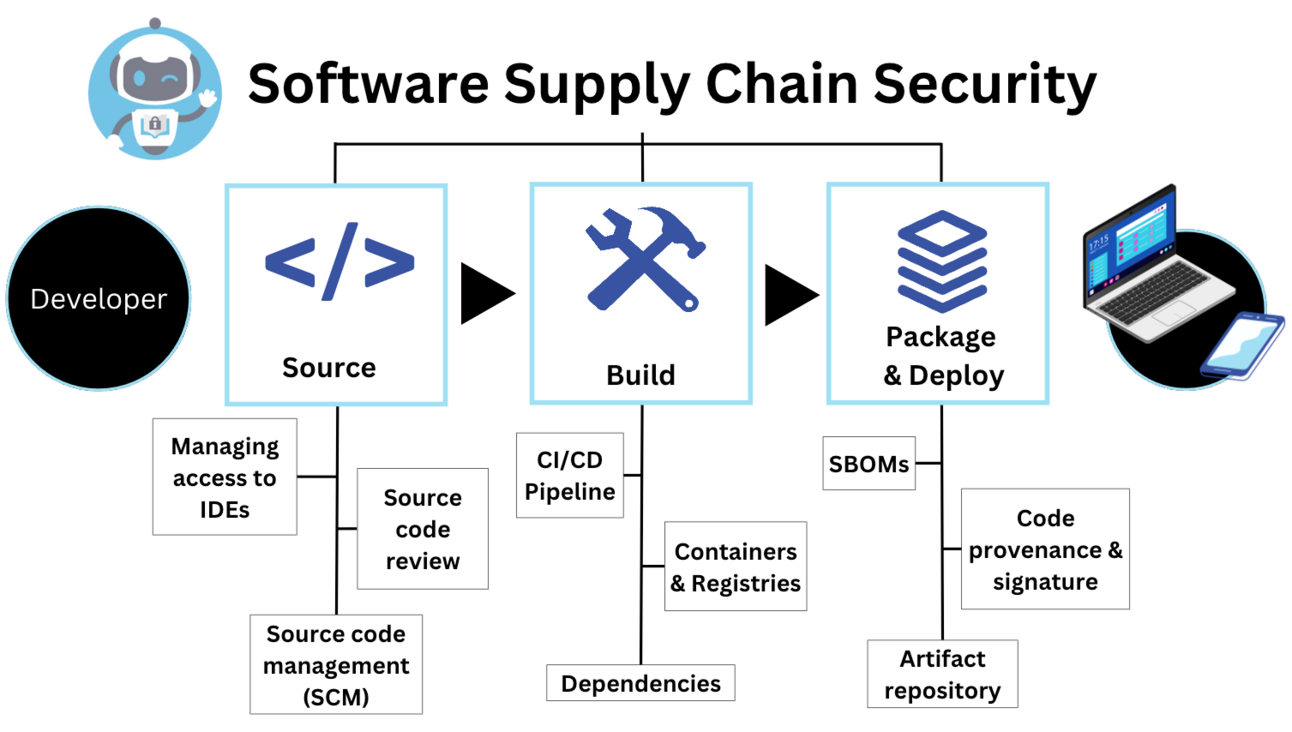
This class of vulnerability has historically enabled some of the most damaging supply chain attacks. Once attackers control the update path they can silently deploy malware with the same privileges as the application itself. In enterprise environments this can lead to widespread compromise across multiple systems in a short period of time.
Patch Details and Security Improvements

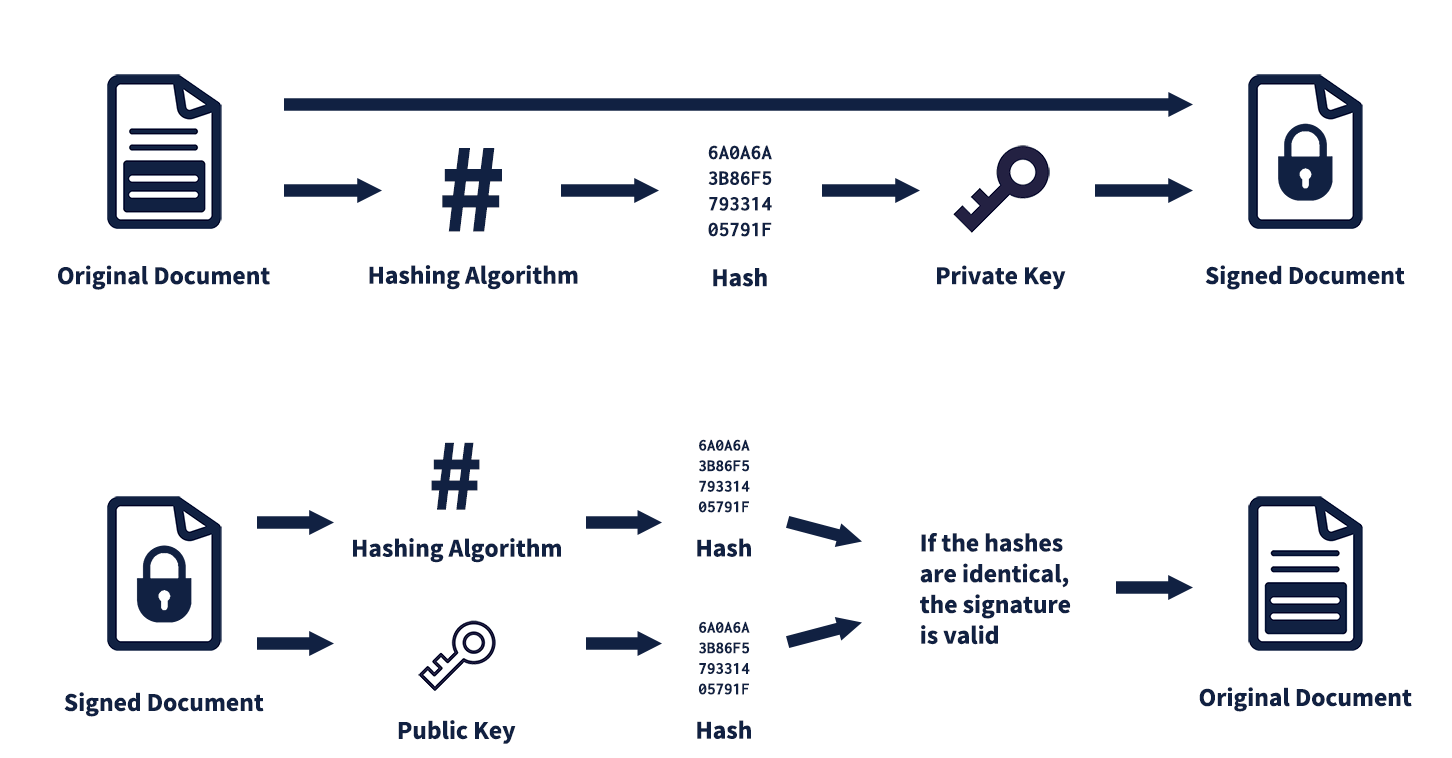
The patched version introduces stronger protections around update delivery and verification. Update requests are now handled in a more secure manner that prevents unauthorized modification of traffic. Additional validation ensures that update metadata and download locations cannot be tampered with by external parties.
These changes significantly reduce the risk of interception and manipulation. By hardening the updater the developers have closed a pathway that could have been abused for malicious distribution even if the core application itself remained secure.
Potential Impact on Users and Organizations


Notepad Plus Plus is widely used by developers administrators and security professionals. Many users rely on it for daily work across development and operational environments. A compromised updater in such a commonly installed tool could have severe downstream consequences.
Affected systems could be exposed to credential theft backdoor installation or lateral movement opportunities. In corporate environments developer machines often have access to source code repositories credentials and internal systems which amplifies the impact of any compromise.
Defensive Actions for Software and Security Teams

Users should immediately ensure they are running the latest patched version and avoid updating software over untrusted networks. Organizations should consider restricting update checks to trusted networks and enforcing application allowlisting where possible.
Security teams should also monitor for anomalous network activity related to update traffic and review endpoint telemetry for signs of unauthorized binaries. This incident reinforces the importance of supply chain security and the need to treat update infrastructure as a critical attack surface.
Final Analysis
The resolution of this updater flaw highlights a recurring lesson in modern cybersecurity. The security of an application extends far beyond its primary codebase. Update mechanisms distribution channels and trust validation processes are equally important.
Traffic hijacking vulnerabilities create silent but powerful opportunities for attackers. By addressing this flaw the developers have removed a critical weakness and reduced the risk of downstream supply chain compromise. Organizations and individuals alike should remain vigilant and ensure that all software updates are delivered through secure and verified channels.
Sign up For Newsletter!!










Leave a Reply