

Google has released an emergency security update for its Chrome browser after confirming the existence of a previously unknown zero day vulnerability that was actively exploited in real world attacks. The flaw was discovered in the wild and exploited before any public disclosure which places it among the most serious browser security threats.
Zero day vulnerabilities represent the highest level of risk because defenders have no prior warning and attackers can operate freely until a patch becomes available. In this case the vulnerability allowed attackers to compromise Chrome users simply by luring them to malicious or weaponized web content. Google has not released full technical details which suggests the flaw was used in targeted operations rather than mass exploitation.
Initial Discovery and Patch Deployment


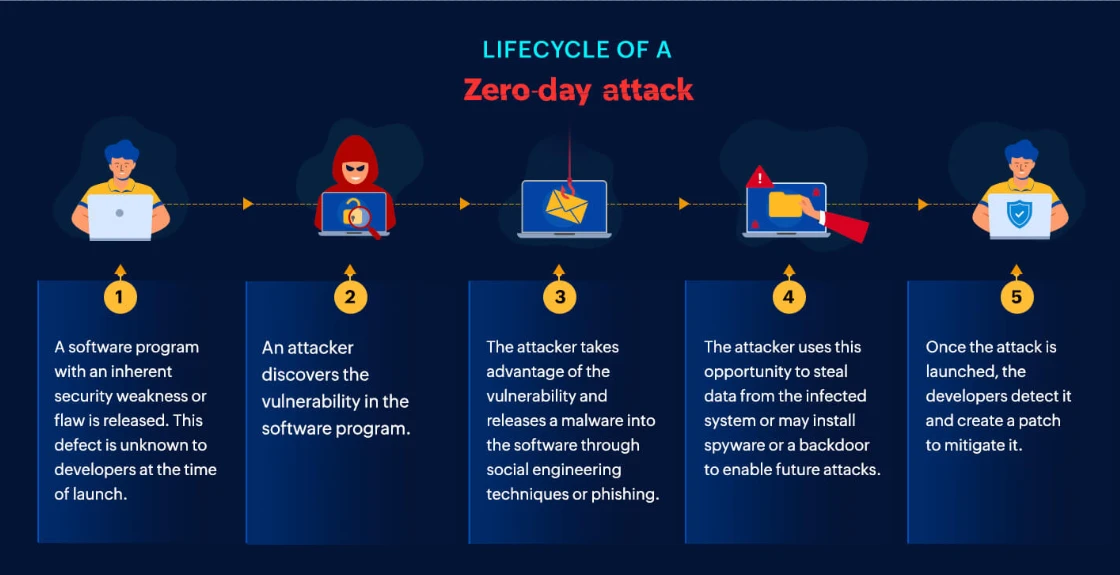
The vulnerability was identified internally and patched rapidly as part of an out of band Chrome security update. Google confirmed that the flaw was being exploited in the wild which indicates that attackers had a functional exploit before defenders were aware of the weakness.
Out of band patches are typically reserved for critical security issues with confirmed exploitation. This response signals that the vulnerability posed a serious threat to users across multiple operating systems. The update was rolled out for Chrome on Windows macOS and Linux and users were strongly advised to restart their browsers immediately to apply the fix.
The lack of detailed disclosure around the vulnerability suggests it may have been leveraged in highly targeted campaigns possibly involving espionage or surveillance operations.
Why Browser Zero Days Are So Dangerous

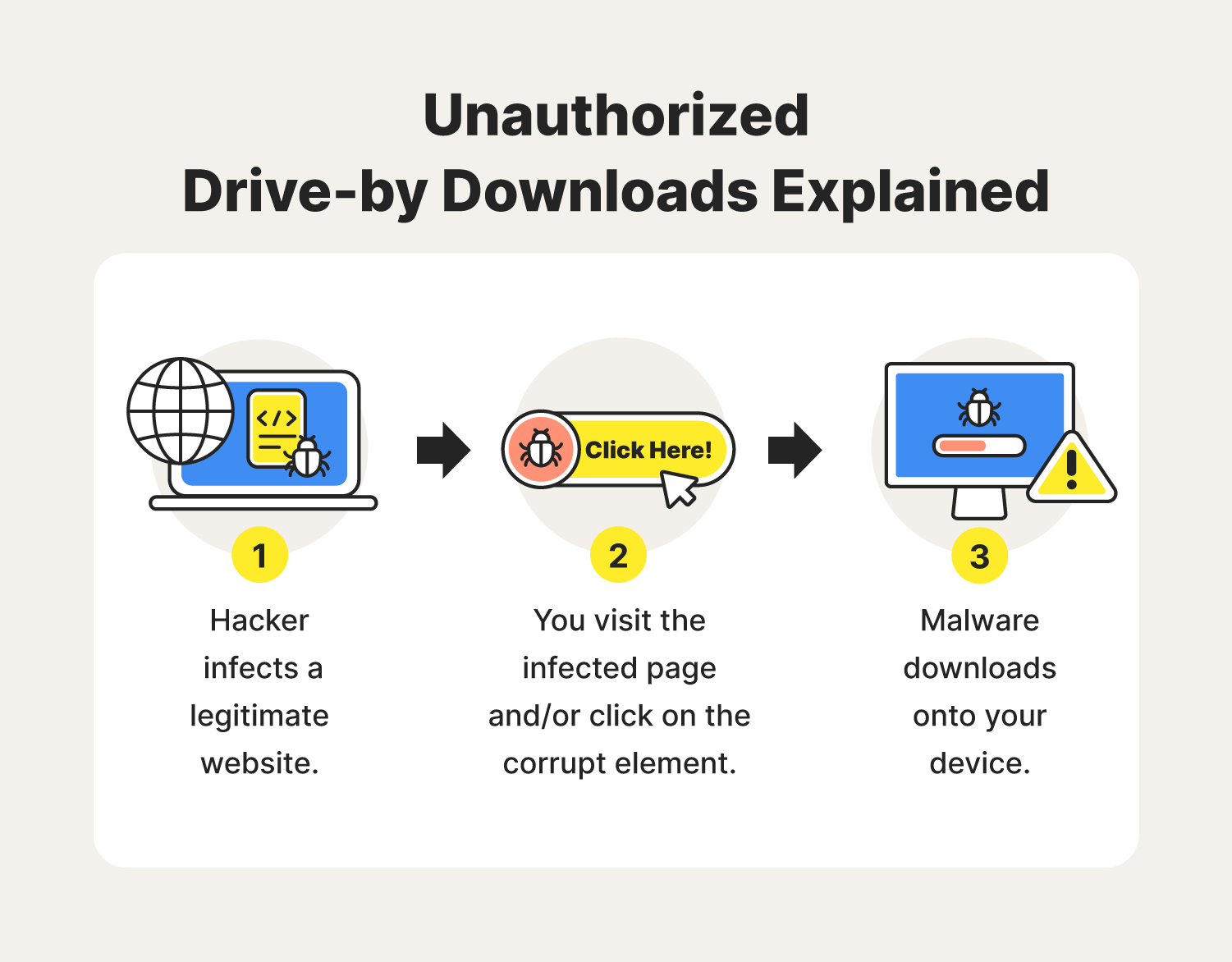

Modern web browsers sit at the center of daily digital activity. They process untrusted content constantly and interact with sensitive data including credentials session tokens and cloud applications. A single exploitable flaw in a browser can become a gateway to full system compromise.
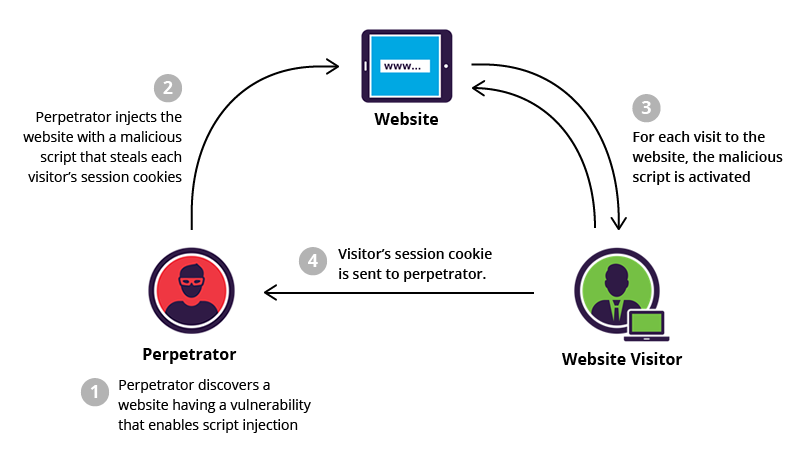
Browser zero days are especially dangerous because they often require little to no user interaction beyond visiting a web page. Attackers can embed exploits into compromised websites malicious advertisements or phishing pages. Once triggered the exploit can execute code within the browser context and in some cases escape browser sandboxes to reach the operating system.
This class of vulnerability is frequently used by advanced threat actors because it enables stealthy initial access without relying on traditional malware delivery techniques.
Possible Exploitation Scenarios



Although Google has not disclosed technical specifics the exploitation scenarios are well understood. Attackers likely used the vulnerability as part of a multi stage attack chain.
Common scenarios include:
Targeted watering hole attacks where legitimate websites are compromised to deliver the exploit
Highly tailored phishing campaigns that direct victims to malicious web pages
Silent drive by exploitation embedded in malicious advertising networks
Use of the exploit as an initial foothold followed by deployment of secondary malware
In advanced campaigns browser exploits are often combined with privilege escalation flaws to move from browser access to full system control.
Who Is Most at Risk

While all Chrome users are potentially affected the highest risk groups include enterprise environments government users journalists activists and individuals involved in sensitive industries. These users are more likely to be targeted by sophisticated attackers capable of acquiring or developing zero day exploits.
In enterprise settings a browser compromise can lead to credential theft access to internal applications and lateral movement across cloud services. Because browsers are trusted endpoints they often have access to single sign on platforms internal portals and administrative dashboards.
Defensive Actions Organizations Should Take



Organizations should treat browser security as a core component of endpoint defense. Immediate actions include:
Ensuring all Chrome installations are fully updated
Enforcing automatic browser updates through device management tools
Restarting browsers to ensure patches are applied
Monitoring endpoints for unusual browser behavior
Restricting browser access to sensitive administrative interfaces
Deploying endpoint detection capable of monitoring browser exploitation behavior
Security teams should also assume that exploitation may have occurred before the patch was applied and review logs for suspicious activity originating from browser processes.
Strategic Implications for Enterprise Security
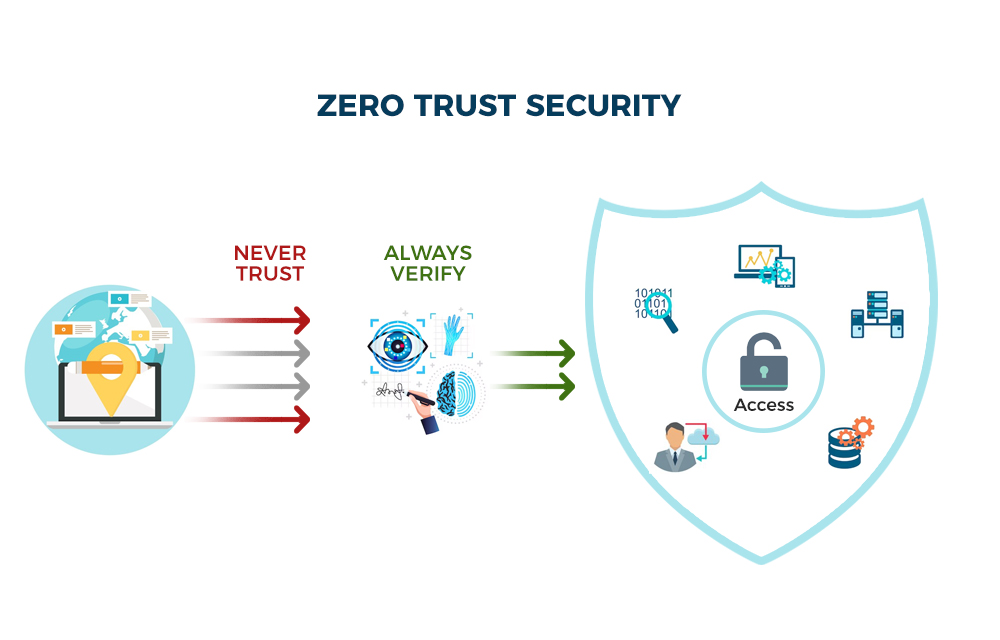

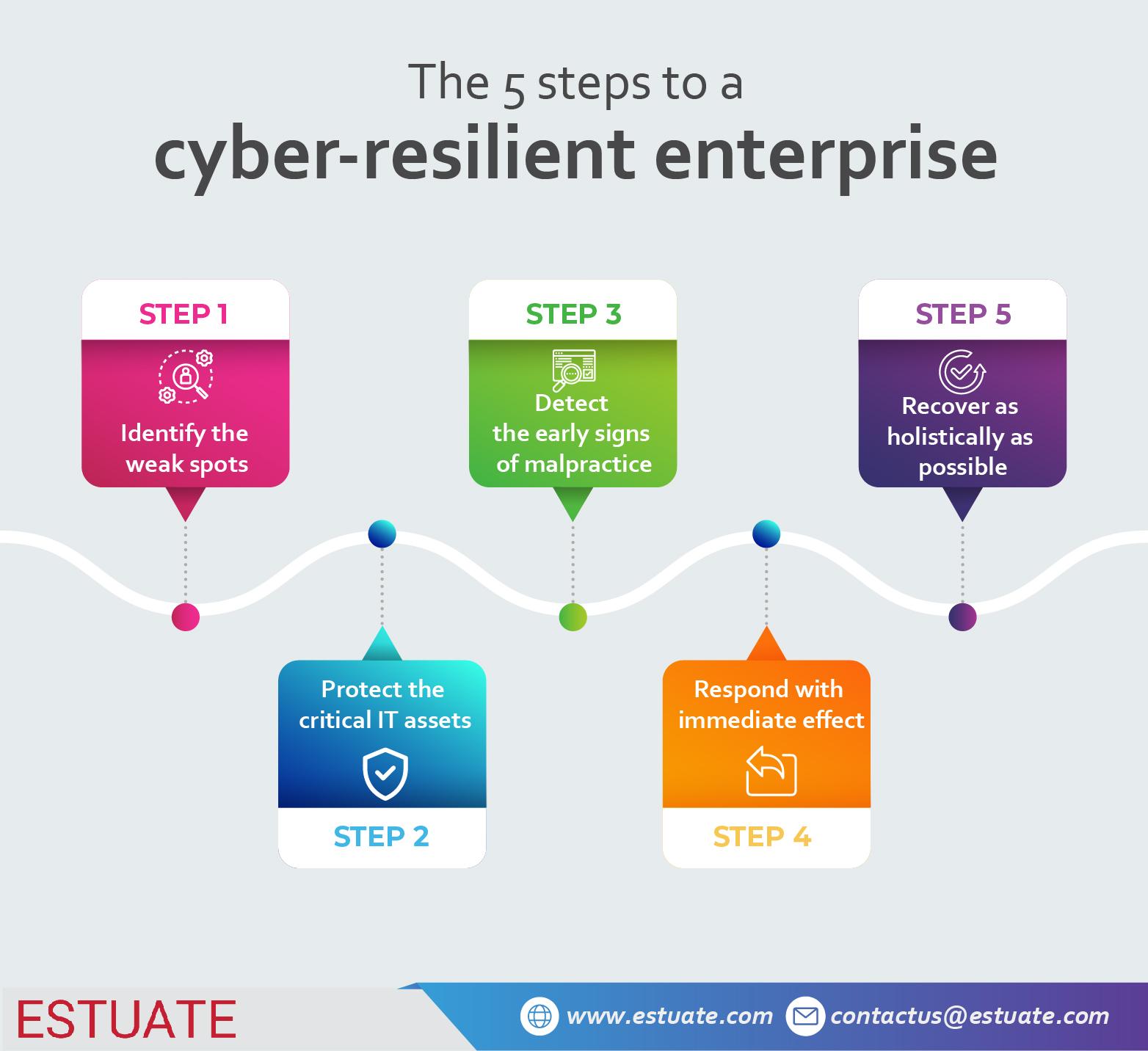
This incident reinforces a critical security reality. Client side applications remain one of the most heavily targeted attack surfaces. Even fully patched systems can be compromised when attackers exploit unknown flaws.
Organizations must adopt layered defenses that assume browsers can be breached. Zero trust principles least privilege access strong monitoring and rapid incident response are essential to limiting damage when a zero day is exploited.
Browser isolation technologies restricted execution environments and continuous monitoring can significantly reduce the impact of future zero day attacks.
Final Analysis
The patching of this mysterious Chrome zero day highlights the ongoing arms race between browser developers and advanced threat actors. As browsers become more complex they remain attractive targets for attackers seeking reliable initial access into modern environments.
The confirmed exploitation of this vulnerability underscores the importance of rapid patching proactive monitoring and treating browser security as a critical component of enterprise defense. Organizations that delay updates or lack visibility into endpoint behavior remain exposed to some of the most dangerous attacks in today’s threat landscape.
Sign up For Newsletter!!










Leave a Reply