
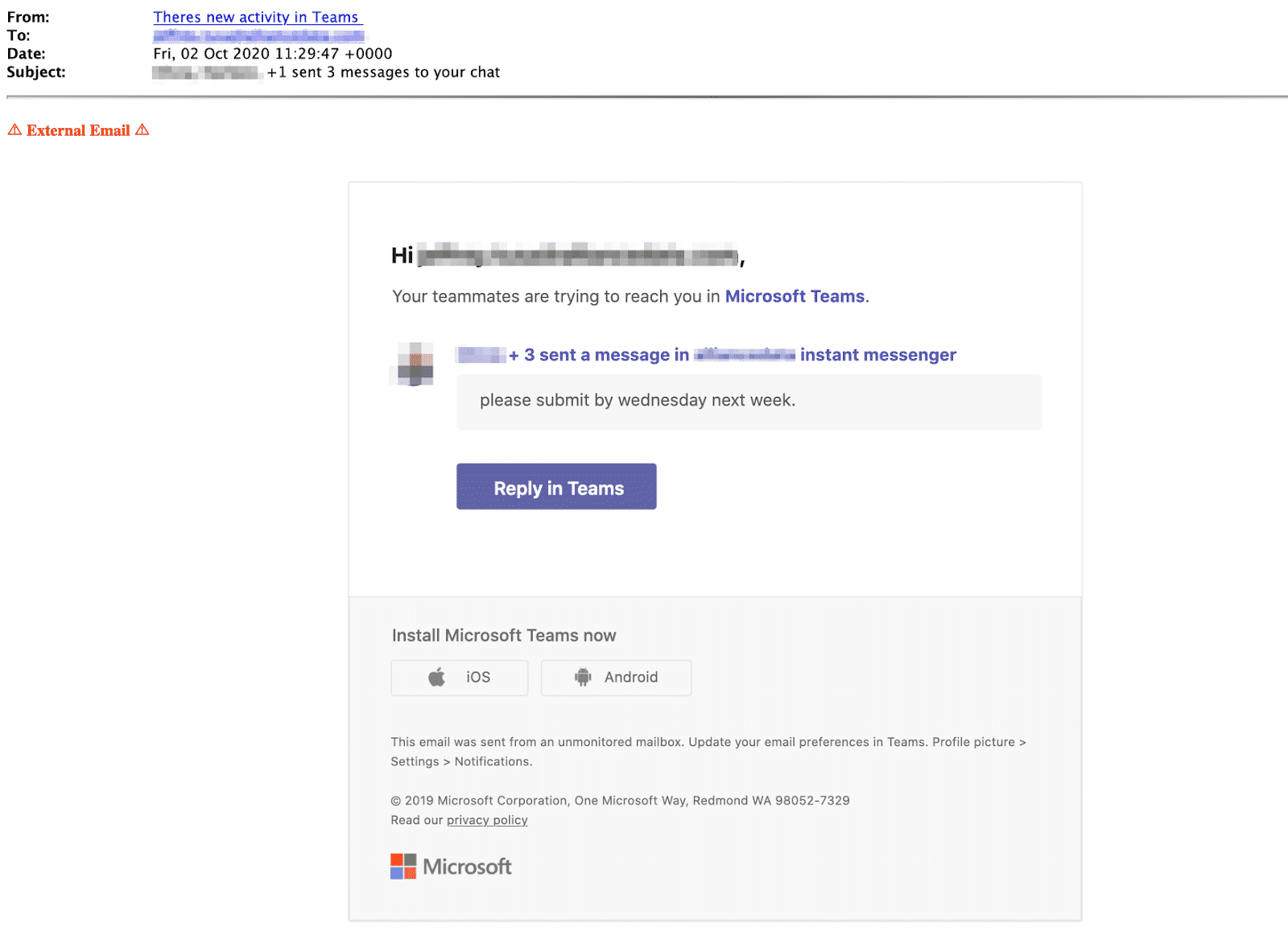
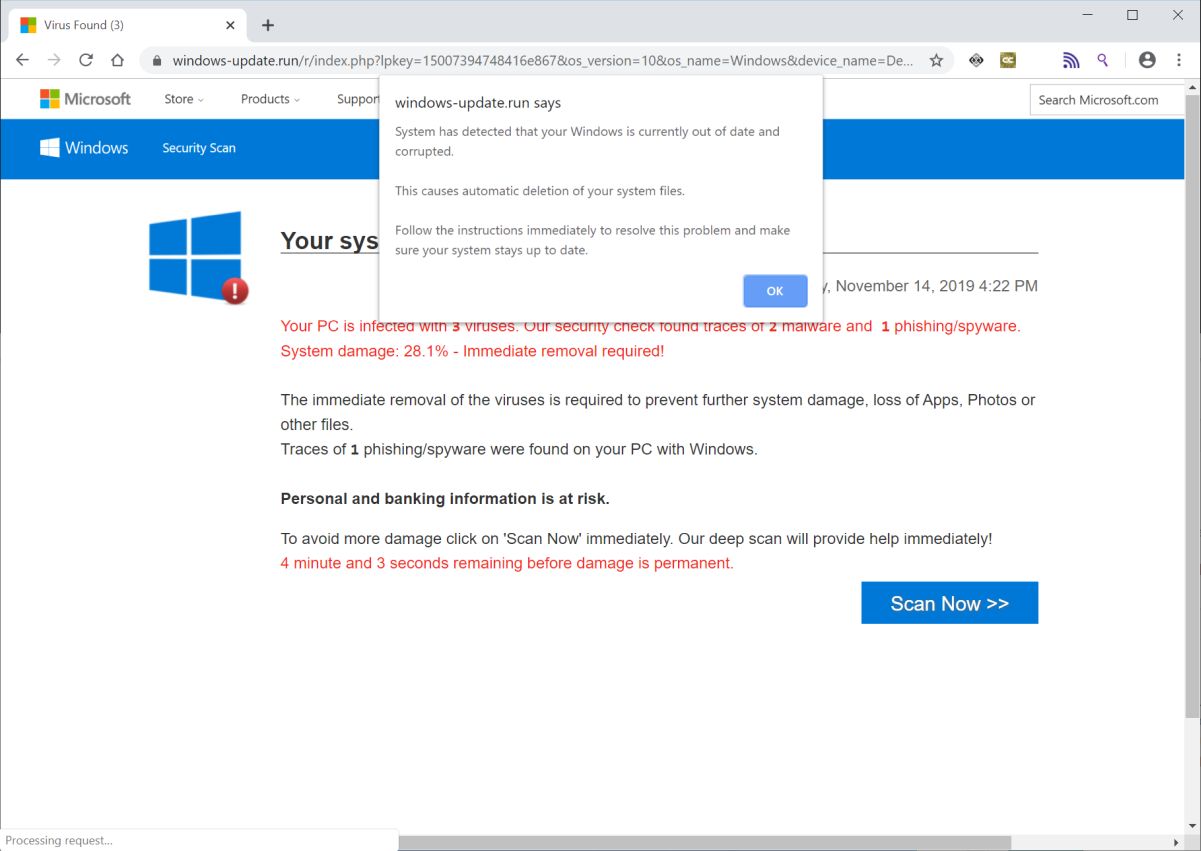
A new wave of cyberattacks linked to the threat group known as Silver Fox is targeting global organizations through deceptive Microsoft Teams update notifications. These fake update prompts are crafted to look identical to legitimate Teams upgrade messages. Once victims click the installer attackers silently deploy backdoors that provide persistent access to the corporate environment.
Silver Fox is known for highly tailored espionage campaigns that blend technical sophistication with precise social engineering. This newest operation shows a deep understanding of enterprise collaboration workflows and how employees interact with trusted productivity applications.
How the Fake Microsoft Teams Update Attack Works


The attack begins when a targeted employee receives what appears to be an urgent Microsoft Teams update alert. The message can appear through email or internal communication channels. The threat actors replicate authentic branding language and formatting to create a sense of legitimacy.
Victims are prompted to download what is described as a mandatory Teams update. Instead of installing collaboration features the downloaded file executes malicious code. This code deploys a stealthy backdoor that allows Silver Fox operators to remotely access the system.
Once installed the malware immediately connects to a command server waits for instructions and allows attackers to monitor the system without detection. The malware is lightweight and avoids creating suspicious behavior that might trigger endpoint detection tools.
The precision of the phishing lure demonstrates that Silver Fox studied how Teams notifications behave and created a clone convincing enough to fool even trained users.
Capabilities of the Silver Fox Backdoor


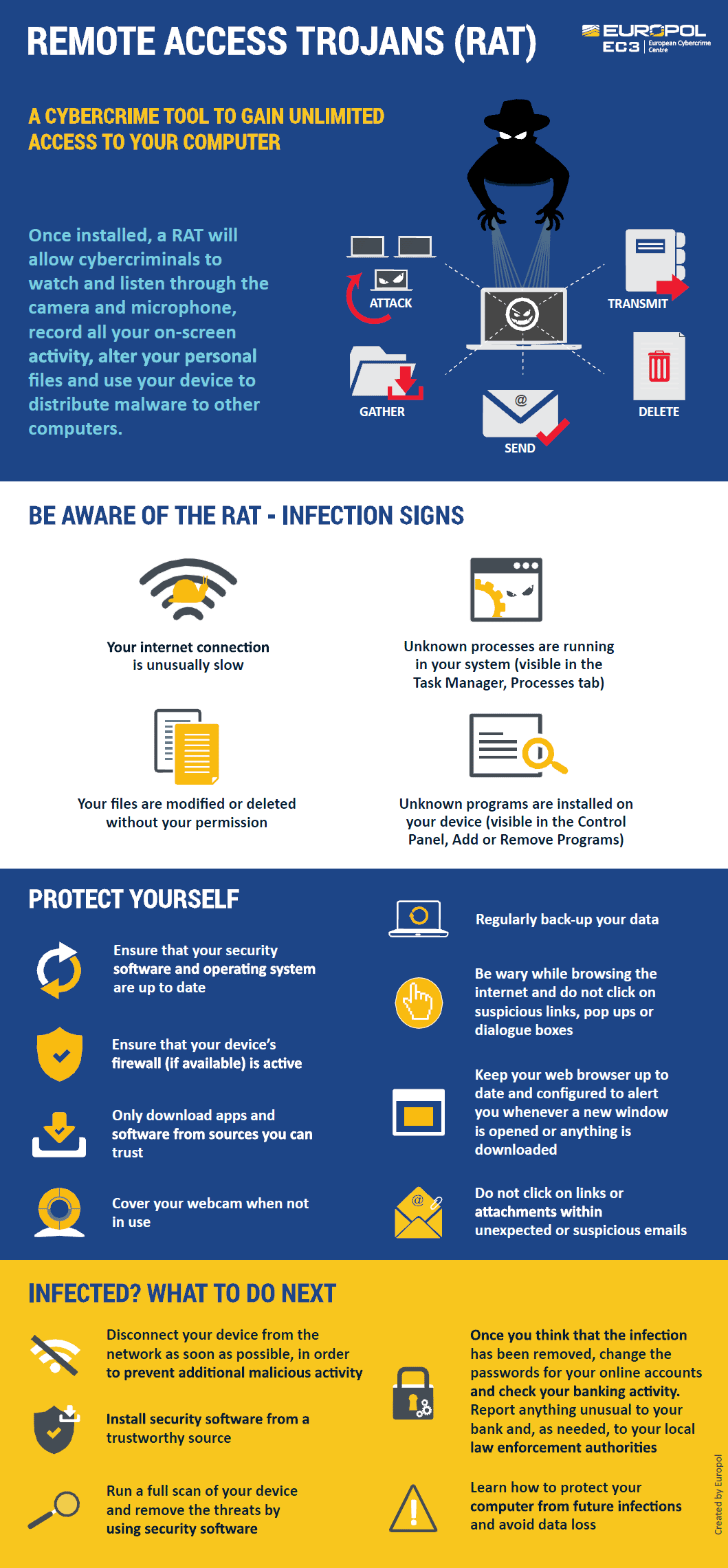
The backdoor deployed by Silver Fox is designed for long term intelligence collection rather than destructive activity. Its capabilities include:
Silent harvesting of documents and internal communications
Credential theft for lateral movement
System reconnaissance to map the environment
Remote command execution
Exfiltration of sensitive information through encrypted channels
Deployment of additional payloads tailored to the victim
Because the malware is disguised as a trusted Teams component it operates under system permissions normally granted to collaboration applications. This gives attackers access to shared drives cloud repositories and internal communications streams.
The operator’s emphasis on persistence and stealth shows that Silver Fox aims to maintain prolonged surveillance inside compromised networks.
Why Microsoft Teams Is an Effective Delivery Channel


Microsoft Teams is deeply integrated into corporate environments and employees are accustomed to receiving frequent updates. This makes it an ideal target for social engineering.
Attackers exploit several psychological and operational factors:
Users trust Teams as a secure enterprise platform
Frequent updates create an expectation of regular prompts
Security teams rarely treat collaboration updates as high risk
Employees prioritize productivity and quickly click update messages
Remote work has increased dependency on collaboration tools
Silver Fox leverages this trust to bypass user skepticism and deliver malware through a workflow that appears normal.
Evidence of Advanced Threat Actor Involvement
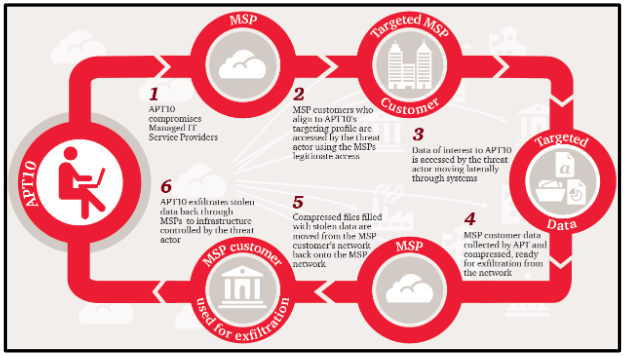


Silver Fox has been linked to high level espionage operations based on its infrastructure command patterns and tool sophistication. The group demonstrates expertise in crafting custom backdoors tailored to specific industries including government energy telecommunications and defense.
Their operations typically involve:
Extensive reconnaissance before issuing phishing lures
Social engineering aligned with real internal processes
Use of legitimate appearing update frameworks
Multi stage payloads designed for stealth
Infrastructure that rotates command servers to evade detection
The fake Teams update scheme aligns with these patterns and confirms that Silver Fox continues to refine its infiltration strategies.
Potential Impact on Organizations


A successful Silver Fox intrusion can have severe consequences across an organization. The backdoor grants attackers wide visibility into internal operations and enables deep infiltration of the network.
Potential impacts include:
Theft of confidential corporate documents
Compromise of executive communications
Lateral movement into cloud resources
Exposure of research data or intellectual property
Tampering with internal systems
Long term espionage and information leakage
Because the malware enters through a trusted update path the compromise may remain undetected for extended periods.
Defensive Measures Organizations Should Take Immediately


Security teams must treat collaboration tool updates as potential attack vectors. Recommended actions include:
Block installation of software not delivered through official enterprise channels
Enable strict application control policies
Verify all update notifications using internal IT guidance
Enforce multi factor authentication to limit credential theft
Monitor network behavior for unusual outbound connections
Deploy advanced endpoint detection capable of analyzing suspicious binaries
Educate employees about fake software update attacks
Organizations should also maintain strict separation between administrative systems and general user workstations to reduce lateral movement opportunities.
Final Analysis
The Silver Fox operation underscores a critical evolution in phishing and malware distribution. Instead of relying on generic lures attackers now mimic trusted enterprise tools so convincingly that even skilled professionals can be deceived. By imitating Microsoft Teams update notifications Silver Fox gains immediate access to corporate systems and establishes durable espionage footholds.
Defenders must elevate awareness around collaboration platform abuse adopt zero trust controls and treat any unsolicited software update as a potential intrusion attempt.
Sign up For Newsletter!!










Leave a Reply