


A major data breach involving the third party analytics provider Marquis has exposed sensitive customer information belonging to more than seventy four United States banks and credit unions. The incident has wide reaching implications because Marquis provides data services to a large portion of the financial sector. Once attackers gained access to the company’s systems they were able to obtain personal and financial information that institutions entrusted to Marquis for analytics and marketing support.
This breach highlights the ongoing challenge faced by financial organizations. Even when their internal systems maintain strong security controls their exposure is often tied to third party vendors. A compromise at a partner can quickly cascade into industry wide risk.
How the Breach Occurred
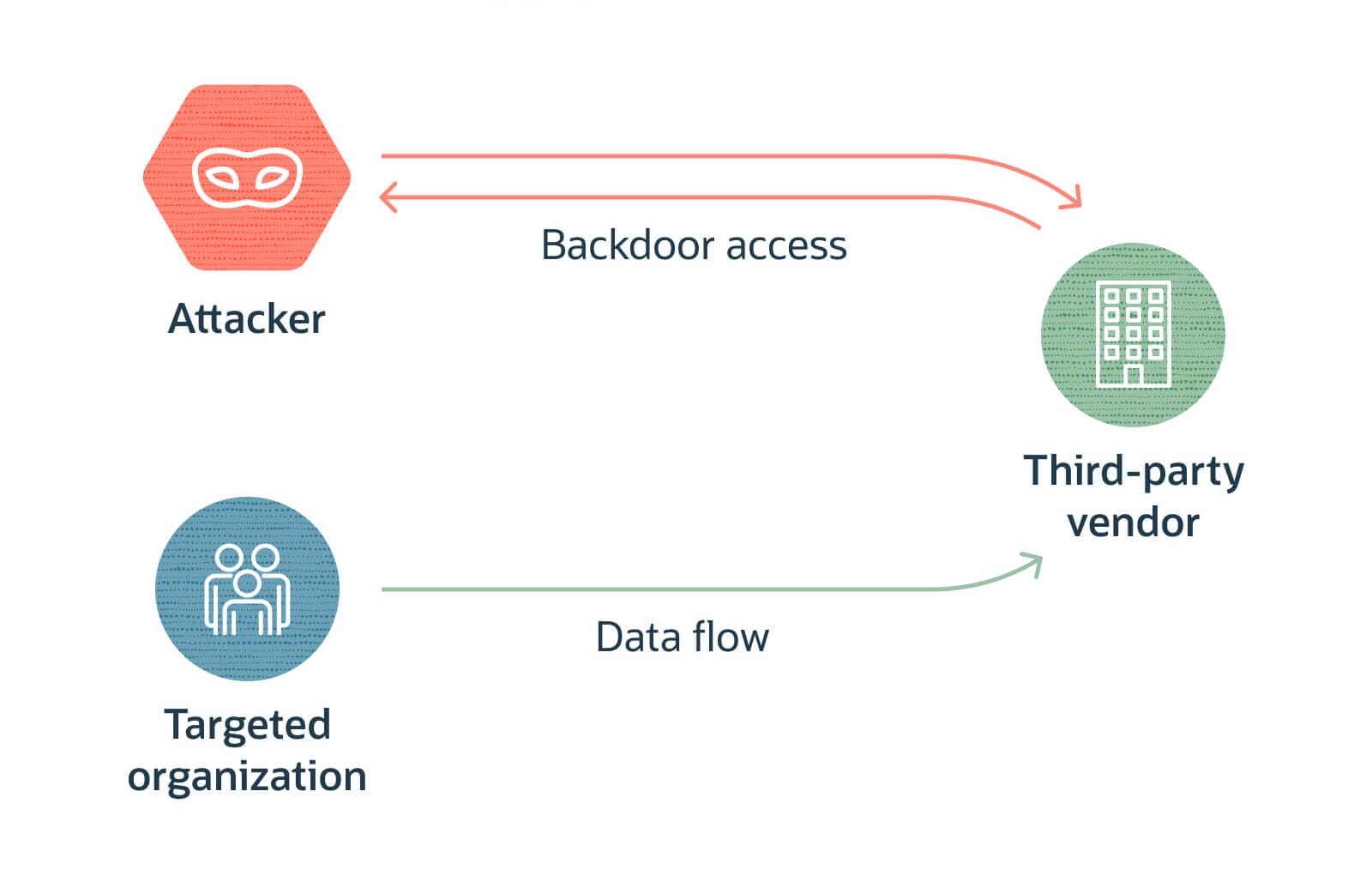

According to incident reports attackers infiltrated the Marquis environment through a compromise of internal systems used to process customer datasets. These datasets contained information provided by client banks and credit unions for account analysis targeted outreach and customer relationship management.
Once inside the environment threat actors were able to access stored data files and extract sensitive records. The stolen information varies by institution but includes:
Full names
Home addresses
Dates of birth
Account numbers
Contact information
Transactional or account relationship insights
In most cases Social Security numbers were not included. However the combination of personal and account related data is more than enough to facilitate identity theft and targeted financial fraud.
The breach went undetected long enough for attackers to exfiltrate a significant volume of files. After identifying the compromise Marquis began notifying affected financial institutions which triggered a cascade of customer notifications across the country.
Scope of Impact Across the US Financial Sector


The scale of this incident is unusually large for a third party data breach. More than seventy four banks and credit unions have confirmed their data was included in the compromised environment. The affected organizations range from small community credit unions to mid sized regional banks, amplifying the exposure across diverse customer bases.
Financial institutions rely heavily on analytics platforms to understand user behavior and improve services. These integrations require sharing customer data at scale. When the vendor is compromised an entire segment of the industry becomes vulnerable at once.
The incident also underscores systemic risk to the national financial ecosystem. Even institutions with strong internal cybersecurity controls remain exposed when third party partners do not maintain equivalent levels of protection.
What Makes This Breach Especially Concerning


Threat actors gaining access to such detailed customer datasets creates multiple high risk scenarios.
The breach may enable:
Account takeover attempts
Phishing campaigns designed to mimic financial institutions
Fraudulent loan or credit applications
Targeted social engineering attacks
Long term identity theft operations
Because the exposed data includes account numbers and other sensitive attributes criminals can craft highly convincing lures. These attacks can bypass standard fraud detection because they leverage real customer details that only institutions or their vendors should possess.
Furthermore financial institutions have regulatory obligations related to customer privacy and data handling. A breach through a third party puts organizations at risk of compliance penalties even though the compromise did not originate within their own systems.
Supply Chain Security Challenges in the Financial Industry

This incident is another example of the broader supply chain vulnerabilities currently affecting critical sectors. Financial organizations depend on a wide ecosystem of vendors for analytics marketing cloud storage and operational services. Each integration introduces another attack vector.
The Marquis breach reinforces key truths:
Trusting third party providers requires stringent oversight
Data handled outside internal systems must remain protected at the same security level as internal data
Attackers increasingly target vendors because breaching one company grants access to many institutions at once
Vendor cybersecurity maturity varies widely across the industry
For financial institutions vendor risk management must be treated as a fundamental pillar of their security posture. A single weak link can generate industry wide consequences.
Recommended Actions for Affected Institutions and Customers

Financial organizations impacted by the breach should take the following steps immediately:
Notify customers promptly with clear information
Enable heightened monitoring for suspicious account activity
Review all data sharing agreements with Marquis
Conduct a full third party security posture assessment
Verify that compromised data has been isolated and secured
Ensure all vendors maintain strict access control and encryption
Customers should take precautions as well:
Review financial statements frequently
Enable account alerts
Use strong multi factor authentication
Be cautious of unsolicited banking emails or phone calls
Monitor for unusual credit activity
While account numbers alone may not be enough to initiate a transaction they greatly increase the effectiveness of targeted scams.
Final Analysis
The breach at Marquis serves as a stark reminder that third party vendors can become significant points of failure for entire industries. More than seventy four banks and credit unions now face potential downstream fraud risks not because of weaknesses in their own infrastructure but because sensitive customer datasets were exposed in an external environment.
As cybercriminals continue to exploit supply chain weaknesses financial institutions must adopt stronger vendor oversight review data sharing practices and ensure that every partner meets the rigorous security standards required to protect customer information.
Sign up For Newsletter!!










Leave a Reply