A serious security flaw in 7 Zip has recently come under active exploitation in the wild. The vulnerability is tracked as CVE-2025-11001 and carries a CVSS score of 7.0, indicating a high level of risk.
What the Flaw Involves
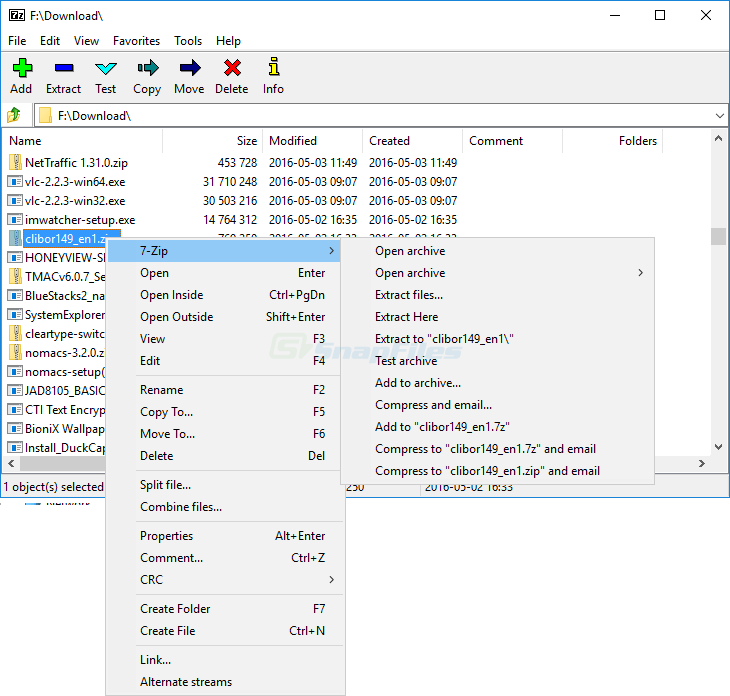
The vulnerability stems from how 7 Zip handles symbolic links inside ZIP archives. Crafted archives can exploit this behavior and cause unintended directory traversal, allowing code execution in the context of a service account.
An attacker who successfully exploits the flaw could execute arbitrary code on a system where 7 Zip is installed and abused, especially if the process is running with elevated privileges.
Versions Affected
The vulnerable versions include those prior to version 25.00 of 7 Zip, which introduced the resolution for this flaw.
Because proof-of-concept code already exists, it is imperative for users to ensure their installations are updated.
What the Exploitation Looks Like
According to advisories, the flaw requires a crafted ZIP file containing symbolic links that can trick the archiver into writing files outside the intended extraction path. One researcher noted that exploitation is only possible if the code is executed in the context of a service account or elevated user on Windows.
Given that 7 Zip is widely used in both consumer and enterprise settings, the risk surface is broad.
Why This Matters for Organisations
Because 7 Zip is a trusted and common tool for compression and extraction, this vulnerability poses a significant threat. Attackers leveraging it can exploit the trust in that tool to penetrate systems, escalate privileges or persist on endpoints.
The fact that active exploitation is already occurring underscores the urgency. Organisations relying on 7 Zip must treat this as a priority patch scenario rather than a mere update convenience.
Steps for Mitigation
- Confirm that all instances of 7 Zip are updated to version 25.00 or greater.
- Identify and inventory systems where 7 Zip is installed, including endpoints and servers.
- Monitor extraction workflows that use ZIP archives from external or untrusted sources and consider enforcing stricter controls.
- Limit the privileges under which extraction tools run and avoid opening ZIP files as service accounts or with elevated rights unless absolutely necessary.
- Train users and administrators to recognise suspicious archive behaviour and avoid executing unknown or unexpected compressed files.
Final Notes
This flaw is a compelling example of how trusted tools can become threat vectors when a subtle bug exists. For cyber defense professionals, this reinforces the need to apply rigorous patching, monitor trusted processes and stay alert to vulnerabilities in widely adopted software.
Sign up For Newsletter!!










Leave a Reply